Original Title: "A&T View: Low Barrier Wallet - A Necessary Tool for Mass Adoption of Web3 Applications"
first level title
Original source:AnT Capital
Summary
TL; DR:
The user experience and security of existing mnemonic wallets are far from the level of Web2. The high threshold of using mnemonic wallets prevents a large number of Web2 users from entering the Web3 world. The mission of the low-threshold wallet is to solve this problem.
The core paradigm of the low-threshold wallet is the 2/2 operation model, which allows the wallet to introduce Web2's mature 2FA, risk control and backup systems, making the user experience and security of the wallet reach the Web2 level, although some solutions partially sacrifice resistance Censorship.
Both low-threshold EOA wallets and low-threshold smart wallets have their own advantages and disadvantages, and both have opportunities in the long run.
Both the supply side and the demand side of the low-threshold wallet track are still in the early stages, and the competition pattern is still undecided, and it is still relatively blue ocean.
first level title
The low-threshold wallet is likely to become the user entrance of Web3, and has the potential to grow into a super Dapp.
preamble
The term wallet does not accurately express its connotation: managing assets like a real-world wallet is just one of its functions. The wallet is essentially a tool for human users to interact with the blockchain. From sending transactions to DAO voting, operations on the user chain almost must be performed through the wallet.
Unfortunately, today's mainstream Web3 wallet—the mnemonic word EOA wallet (represented by Metamask) is extremely poor in ease of use, and this threshold prevents a large number of Web2 users from entering. For a Web2 novice, when he enters Web3 to use the Metamask wallet for the first time, a long list of mnemonic words and a warm reminder of "never disclose the mnemonic words to others" will come into the user's eyes. At this time, the user remembered the various wallet private key theft tragedies he had heard, so the user hurriedly found a piece of paper and copied the mnemonic, and then hid it in his drawer. Immediately afterwards, he discovered that he didn't have any eth, which meant he couldn't perform arbitrary operations.
So he had no choice but to click on Metamask's fiat currency deposit function, fill in various bank card information and obtain the corresponding eth. At this time, he can finally start playing his pet cat game on the chain, and he must always be vigilant about whether the use environment is safe and whether the mnemonic is leaked. Of course, the above are very idealized situations. The real situation is more likely to be that 80% of users give up account registration when they see the mnemonic, and 80% of the remaining 20% users leave Web3 before making a deposit. .
If a product wants to gain mass adoption by the public, it must lower its user threshold. Computers 50 years ago had similar (but more extreme) problems to Web3 today. The situation of Web3 is that the threshold for using tools (wallets) for human users to interact with the blockchain is too high, while the threshold for early computers is too high for the interface between human users and computers: early computers only supported command line interfaces.
image description
image description
Apple was the first to promote the graphical interface, bringing computers into the world of the masses
The same is true for Web3, only when the operating threshold between users and the blockchain is lowered to a certain level, such as having a product experience similar to Web2, can Web3 products be adopted on a large scale, otherwise it will appear that the number of investors > the number of project parties > The number of users. Therefore, if Web3 is to be accepted by the public, the wallet threshold must be lowered, and this is the mission of the low-threshold wallet.
first level title
A Paradigm Shift for Low-Barrier Wallets: Web2-Level Security and User Experience
Low-threshold wallets and ordinary mnemonic wallets are two completely different paradigms.
The operation model of the mnemonic wallet is that whoever owns the private key (mnemonic) has full ownership and management rights of the account assets. Compared with Web2 with two-factor authentication and password retrieval, this operation model first greatly damages the security of user assets: whether the private key is stolen or lost, the user will lose all assets; Damage to the user's product experience: Users need to spend a lot of effort to prevent the mnemonic from being stolen/lost, such as having to write the mnemonic on paper and hide it. Of course, the benefits are also obvious, that is, users have asset sovereignty and do not have to worry about evil or censorship by centralized institutions.
The low-threshold wallet uses a brand new2/2 operating modelsecondary title
The core of the low-threshold wallet: 2/2 operation model
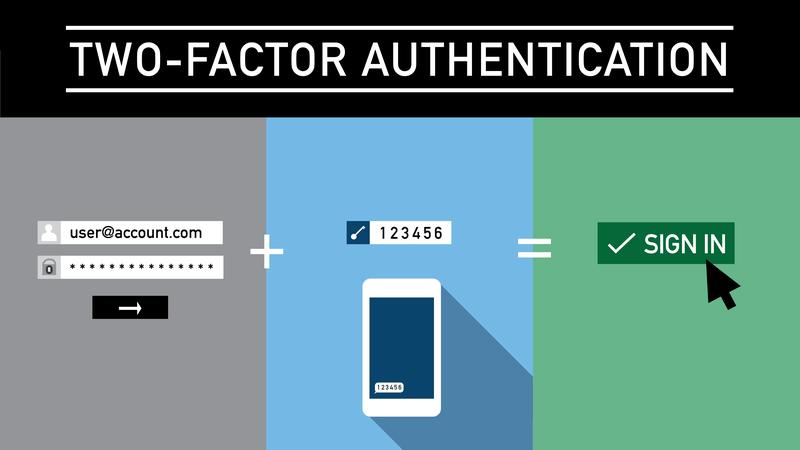
In simple terms, the 2/2 operation model means that all user operations must be approved by the designated 2 parties. The simplest implementation is to use a multi-signature wallet, and it is stipulated that each operation of the wallet must be signed by two private keys. If we assign the two parties as the client side and the wallet project side (the specific implementation of the multi-signature wallet solution is to store a private key in the user's mobile device, and the other private key is stored in the server of the wallet project side) ), which means that if the wallet project party does not agree, an operation cannot be completed. On this basis, the wallet project party can use the already mature Web22FA (two-factor authentication) and risk control technology raise the security of the wallet to the Web2 level.
2FA (Two Factor Authentication):In Web2, when a user logs in an account on a new device, usually the Web2 application will perform additional verification on the user, such as email verification, SMS verification, device verification, face recognition verification, etc. The security assumption here is that hackers cannot crack two different authentication factors of a user at the same time. In fact, this is why Web2 user accounts are far more secure than mnemonic wallet accounts.
And now the server of the Web3 wallet project can help users do the same two-factor authentication as the Web2 application—only when the user passes the verification, the wallet project allows the user to operate on the new device. This makes it possible that even if the private key on the user side is stolen, the security of the user's property can be guaranteed because the hacker does not have the second authentication factors such as the user's mailbox, mobile phone, and face.
Risk control: In Web2, a powerful risk control system can prevent most of the asset theft and fraud. For example, AlphaRisk, the risk control system behind China's top payment company Alipay, will conduct multi-dimensional risk detection on each transaction. Behind the system are nearly 500 quantitative strategies and 100 risk models to accurately identify abnormal behavior of user accounts.
Now, the server of the Web3 wallet project side can help users run Web3's exclusive risk control system, and provide reminders and multiple verifications for users who are about to participate in suspicious transactions, so as to greatly reduce users' being defrauded in the Web3 "dark forest". Risk of fishing or property theft.
After the user's security is upgraded to the Web2 level, the user can simply back up their private key to the user's own cloud disk, such as Google drive or iCloud, thereby reducing the risk of private key loss and allowing the user toNo need to recite/copy mnemonic words, greatly lowering the threshold. In this step, the user can directly back up the private key and mnemonic, but the essential reason why ordinary wallets cannot be: because the security of the low-threshold wallet has been upgraded to the Web2 level, even if the user’s private key is lost, the user’s assets will not be lost. There will be losses.
If readers think this is a bit counter-intuitive, here is another completely similar example, that is why we can set such a simple and regular 8-digit password in the Web2 application (compared to the completely random 64-bit hexadecimal Ethereum Private key, which is too easy to be compromised) The essential reason is that we have Web2's 2FA and risk control to ensure the security of our account.
In addition to the need for mnemonic words, the 2/2 operation model also allows the wallet to be embedded in dapps, so that users do not need to jump to the wallet application when performing dapp operations, thereby greatly improving the user experience. Why is it impossible for the mnemonic wallet to be embedded in the application? Because embedding means that the wallet provides its own sdk to the application project party (otherwise, when the user clicks "buy" in the application, how can the application sign for the user to directly purchase the item), at this time the application has user-side privacy. Full control of the key.
In the 2/2 operation model, if the risk control system of the wallet project party detects suspicious transactions, such as suspecting that the application is stealing user assets, the wallet project party can ask the user to do a second verification, such as sending an email verification code to confirm that this operation is made by users. But in the operation model of the mnemonic wallet, no one can prevent the application from stealing the user's assets.
So far, the low-threshold wallet based on the 2/2 operation model has raised wallet security and user experience to the Web2 level.The final user process is, like the familiar Web2, log in with google/mobile phone number/email at the beginning, and then you can use it directly.When the user needs to back up the private key, just click "Backup", and then the private key on the client side will be automatically backed up to the cloud disk. But we have always had an assumption before: the centralized wallet project party has been providing its services with due diligence. Now is the time to consider the possibility of centralized wallet projects doing evil.
The first question is, can wallet project parties steal users' funds like escrow wallets?
The answer is no. The 2/2 operation model of the low-threshold wallet stipulates that each operation must obtain the consent of both the client and the wallet. As long as the user does not cooperate, the wallet project party cannot transfer the user's assets privately.
The second question is, can the wallet project party freeze user assets?
The answer is, yes, if the functionality of this wallet ends there. The 2/2 operation model of the low-threshold wallet stipulates that each operation must obtain the consent of both the user end and the wallet end. As long as the wallet project party does not cooperate, the user will never be able to make any operations. This sounds like a very serious problem, but I think it is acceptable for Web2 novice, because the wallet project party actually does not have much economic incentive to freeze the user's account. If it is really frozen, the probability is greater It's because of censorship.
secondary title
2/2 Implementation method of operation model
The 2/2 operation model has nothing to do with the type of wallet. Whether it is a smart wallet or an EOA wallet, you can use the above 2/2 operation model to transform into a low-threshold wallet, but the characteristics are different.
There are two main methods for the EOA wallet to implement the 2/2 operation model: Shamir's Secret Sharing and MPC.
The Shamir's Secret Sharing scheme simply divides the original EOA private key into two pieces and distributes them to two parties. When they need to use them, the two parties send their respective private key pieces to the same device and aggregate them into the original complete private key. , and then sign with this full private key. However, because the Shamir's Secret Sharing scheme has a private key aggregation step, if the aggregation device is hacked, the complete private key will be directly stolen, which increases the security risk.
MPC (multi-party secure computing) technology solves this problem: both parties of the 2/2 operation model will directly generate private key fragments in their respective devices, and the two parties cooperate to directly generate signatures during operation, instead of aggregating into a complete private key first. key to sign again. This means that if our mobile phone for wallet operations is hacked, using the Shamir's Secret Sharing scheme will lead to asset theft, while using the MPC scheme will not cause security incidents.

secondary title
Low threshold smart wallet VS low threshold EOA wallet
The difference between a smart wallet and an EOA wallet is that its ontology is a smart contract, so arbitrary logic can be implemented. People who support smart wallets or account abstraction will talk about its many new features, such as Multicall, Session keys, etc., but I think the most important thing is that smart wallets haveSocial recovery function on the whole chain, many other functions can be satisfied by the 2/2 operation model.
In other words, as long as the user has bound several friends/family on the chain, when the wallet project party wants to freeze the user's assets, as long as the user's friend/family account is still available, it can help the user complete the account on the entire chain. Recovery, ultimately allowing the user to regain control of the account. This is how the low-threshold smart wallet solves the problem that wallet project parties have the right to freeze user accounts. If the EOA wallet wants to prevent user accounts from being frozen, although there are some solutions, the overall difficulty is much greater.
There are also many disadvantages of smart wallets compared to EOA wallets:
1) It is difficult to support multiple chains: the contract of the contract wallet is bound to the public chain system, that is to say, when deploying a smart wallet on a chain with a different structure, the account logic needs to be redeveloped, and the cost is very high. And the generated accounts are completely non-universal because of the different structure. In fact, almost all smart wallets now only support the EVM chain.
2) Gas is more expensive: the logic of the smart wallet is more complicated than that of the EOA wallet, so the gas for each operation will be more expensive. In addition, creating a smart wallet also requires a lot of gas fees.
3) Not yet widely promoted: All applications now accept the EOA account system, but not necessarily the contract account system.
Among them, I think problem 2) and problem 3) will be solved in the long run, and 1) is indeed a flaw of the smart wallet.
secondary title
competitive landscape
The track is in the early stage, and the core competitiveness is product capability and BD capability
It's still early days for the low-barrier track. The early stage here can be divided into two dimensions, 1) the supply side is in the early stage, and 2) the demand side is in the early stage.
The early stage of the supply side means that the product design of the low-threshold wallet has not yet been finalized. Everyone is still doing tradeoffs in terms of user experience, security and anti-censorship, and is constantly exploring new functions. An example is that Web3auth, which has been established for two years and has been led by Sequoia and other large capitals, recently abandoned the previously inefficient 5/9 consensus model and changed to the more advanced mpc model, which fully proves that this field The supply side is still in an unstable, high-speed iteration state.
The demand side is in the early stage, which means that the customer base of the low-threshold wallet is a large number of Web2 novice users who will be brought into the Web3 world when Web3 applications explode on a large scale in the future. Now the users of wallets are all investors and builders who come to make money and learn, and are completely different from the user portraits of "Web2 novice users" who come for user experience. Therefore, the market is still in the early stage, and low-threshold wallets are expected The captured Web2 novice users have not yet appeared.
When the supply side is still in the early stage and the product has not yet been finalized, the product capability of a project is very important. This is also the point where the project is easy to differentiate. Therefore, the product capability of the project is one of the core competitiveness. The second core competitiveness is the projectBD ability: First of all, we assume that these Web2 novice users are brought by Web3 applications, so in fact, what wallet a user chooses to use to enter the Web3 world is almost entirely dependent on the wallet that the first Dapp it contacts chooses to embed.
secondary title
Sort out some existing projects
secondary title
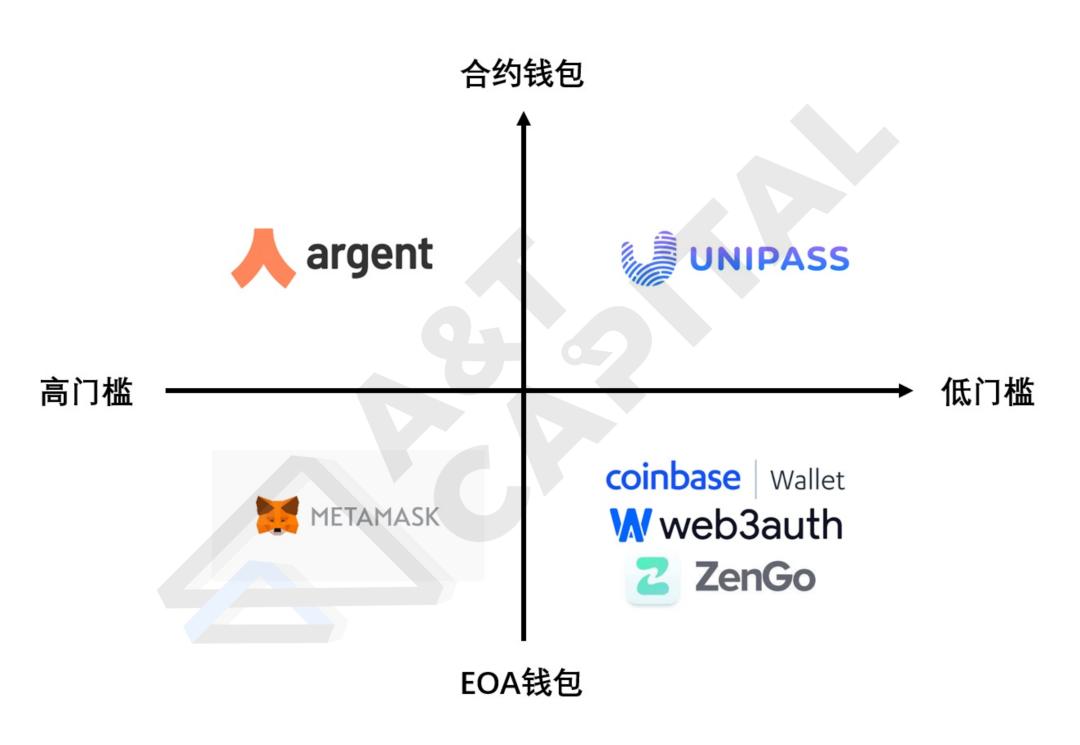
Web3auth:
Web3auth is a mature low-threshold wallet company. The latest round has received $13 million in investment from large institutions such as Sequoia India, USV, Multicoin, and FTX, which has brought Web3auth a good BD advantage. Its current flagship product, Torus, adopts a 5/9 consensus to help users save their private keys so as to be helpless to remember words. However, the complex consensus makes users need to wait 30-45 seconds for login, which greatly damages the user experience, so Web3auth is now under development The low-threshold EOA wallet based on the MPC 2/2 operation model is expected to be launched by the end of the year.
secondary title
ZenGo:
secondary title
Coinbase Wallet:
Coinbase Wallet is a low-threshold wallet launched by Coinbase, and it is also a low-threshold EOA wallet based on the 2/2 operation model of MPC. It is worth noting that Coinbase Wallet is mainly a to C wallet, rather than Dapp integration like other low-threshold wallets. However, based on the author's assumption that a large number of Web2 novice users will be captured by the application, it may not be a good direction to focus on doing to C.
secondary title
UniPass:
UniPass is an emerging low-entry wallet company, the latest multi-million dollar round of financing. UniPass' product is a low-threshold wallet based on the smart wallet's MPC 2/2 operating model. Because UniPass is a smart wallet, it can solve the problem that the wallet project party has the ability to freeze user assets: UniPass innovatively allows users to bind the mailboxes of relatives and friends on the chain. If an extreme situation occurs, the wallet project party freezes User assets, users can also calmly use the mailboxes of relatives and friends to reset the account, so as to regain control of assets.
secondary title
Argent:
first level title
first,
first,Web3 applications that want to gain mass adoption will definitely adopt low-threshold wallets.The reason is simple. The mnemonic EOA wallet will greatly reduce the user experience of Web2 Xiaobai, and it will greatly reduce the conversion rate of Dapp. Users will immediately return to the user comfort zone of Web2. The low-threshold wallet solves this problem to a large extent. Users only need to use familiar mailboxes, phone numbers, Google and other login methods to interact with dapps safely and smoothly. This provides the possibility for most Web3 Dapps to compete with Web2 apps with excellent user experience on a large scale.
Well, if in the next bull market, Web3 really ushers in the explosion of applications, and a large number of users enter the Web3 world through applications, the low-threshold wallet will become the traffic entrance for large-scale users to enter web3, which means that the low-threshold wallet will have a large number of Users: If the explosion of the Web3 application layer brings 100 million users to the Web3 world, there is a high probability that 80 million users will use low-threshold wallets.
At the same time, after Web3 Dapp has occupied our lives, the interaction between users and the blockchain is likely to be high-frequency, which means that the wallet can do a lot of extension functions, and may even become a Web3 super APP. For example, WeChat has a large number of users, and users use it frequently. WeChat can embed many functions, such as WeChat payment, WeChat official account, WeChat login, etc., and finally build a super business empire. Similarly, the wallet also has the potential to build a super ecology by virtue of its ecological niche of user entrance.