foreword
On June 8, 2022, Beijing time,Know Chuangyu Blockchain Security LabKnow Chuangyu Blockchain Security Lab"Public depositFromOtherContract"The authority control issue was attacked, and the loss included 7,475 BNB, totaling about 216W USD. At present, the ETH exchanged for 70W USD through DEX has been cross-chained to Ethereum through Celer. 2,000 BNB are mixed using BSC-Tornado, and the remaining 3,000 BNB at the attacker address.
Know Chuangyu Blockchain Security LabFollow up and analyze this incident as soon as possible.
basic information
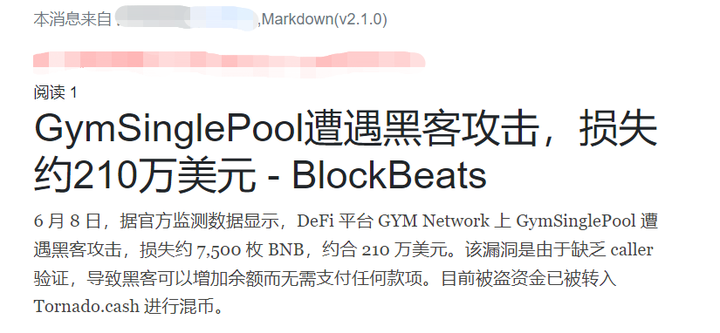
basic information
Attacked contract: 0x0288fba0bf19072d30490a0f3c81cd9b0634258a
Attacker address: 0xB2C035eee03b821cBe78644E5dA8B8eaA711D2e5
tx:0xfffd3aca0f53715f4c76c4ff1417ec8e8d00928fe0dbc20c89d875a893c29d89
GymSinglePool proxy contract: 0xa8987285e100a8b557f06a7889f79e0064b359f2
Vulnerability analysis
Vulnerability analysis

During the implementation process of the GymSinglePool contract, the project party lacks permission control for the 0x0288fba0bf19072d30490a0f3c81cd9b0634258a#depositFromOtherContract function, which allows attackers to call the internal _autoDeposit function through this function to achieve zero-consumption pledge:
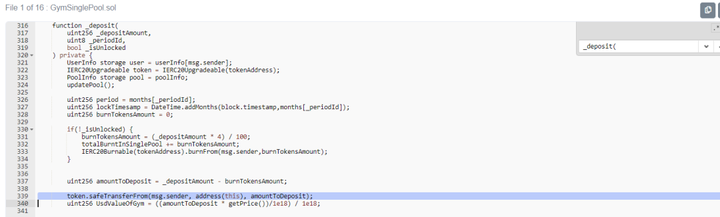
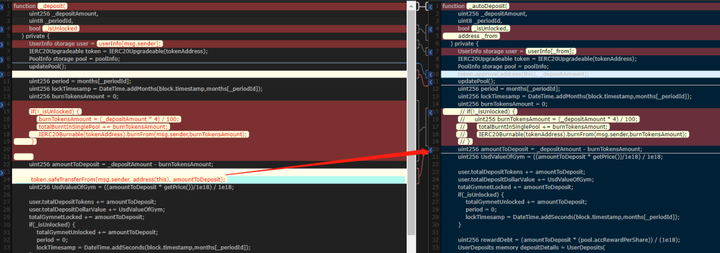
The internal function of the pledge that should be open to users is the _deposit function, which implements the approval of tokens, as shown in the following figure:"The corresponding _autoDeposit function implements"Pledge, that is, there is no need to transfer Token for pledge. At the same time, the function is directly exposed to the user. The function comparison is as follows:
attack process
attack process
In order to prevent the on-chain MEV and preemptive robots, the attacker deployed and executed the contract step by step, and deployed/called multiple times at the same time to complete the complete extraction of the GYMNET Token in the GymNetwork contract (0x3a0d9d7764FAE860A659eb96A500F1323b411e68), and one of the deployment calls For example:"1. After deploying the contract, call depositFromOtherContract"privilege
Pledge, corresponding to 0xfd4a2266 method:
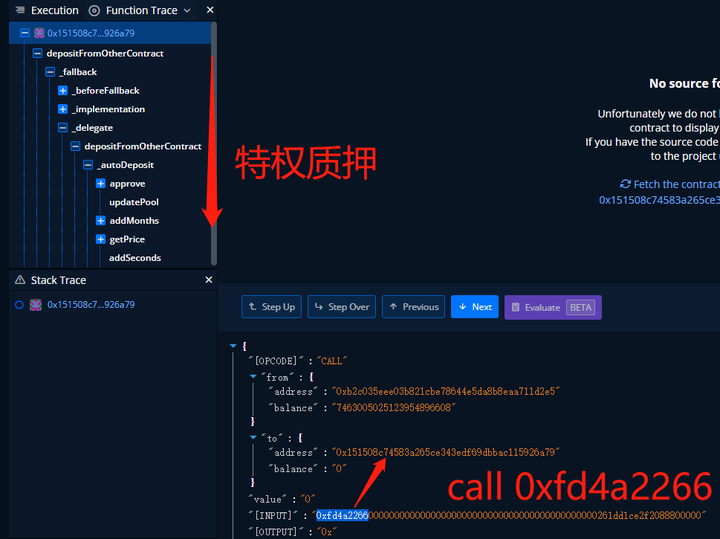
The internal call details are as follows:
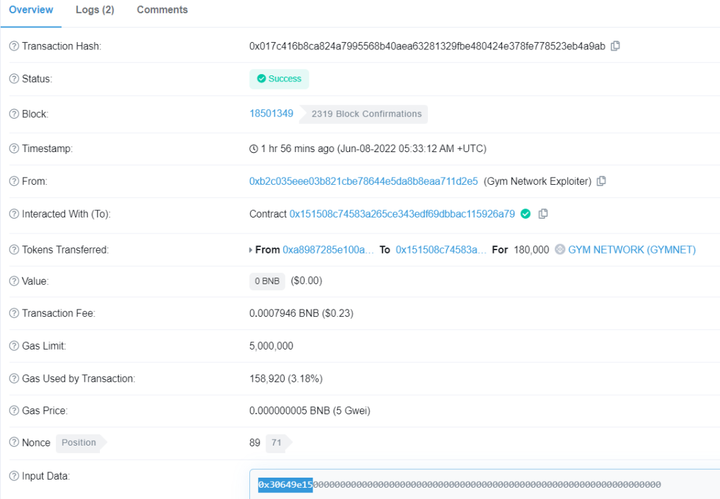
2. Call 0x30649e15 to realize the Token withdrawal of the previous privilege pledge:
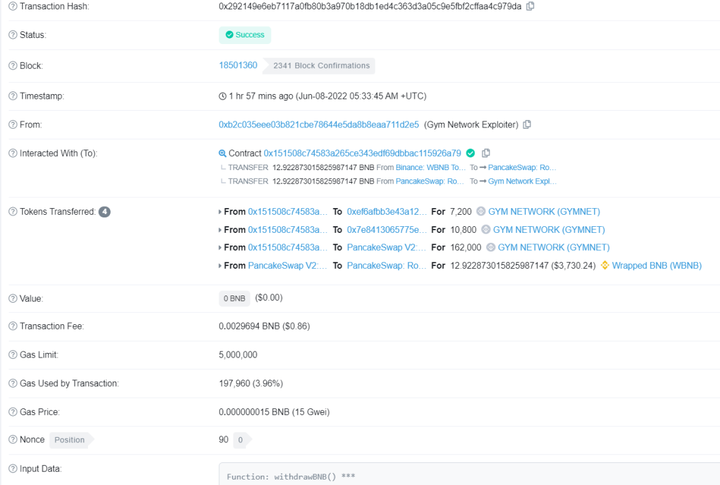
3. Use the 0x1d111d13 function to sell the acquired GYM-Token:"repeat many times"privilege
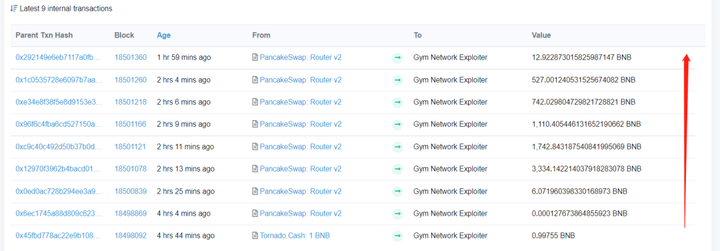
Pledge--withdrawal--sell steps, the attacker finally obtained 7475 BNB:
In order to suppress front-running, the attacker separated the steps of adding pledge and withdrawing. Both steps are core operations. At the same time, the Gas Price of adding some steps was deliberately increased to 15/20gwei, which shows that the attacker did it intentionally.
Traceability
The reason for this attack is that the privileged function authority control implemented by the project party was improper. One hour after the attack was discovered, the project party modified the logic contract of the GymSinglePool proxy contract several times and added authority control to it:
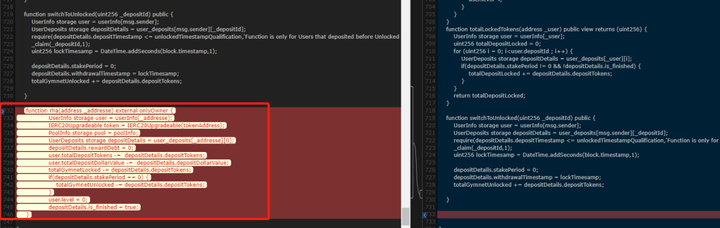
And add an emergency account disposal function to the logic contract after 20 minutes:
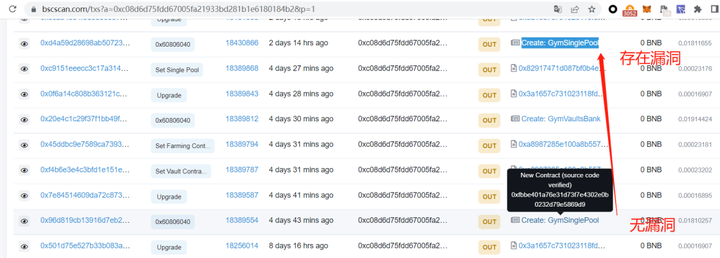
As for the Deployer address analysis of the project party, the multiple GymSinglePool contracts deployed by it only have loopholes in the GymSinglePool contract deployed two days ago according to the tracking, and the contract 4 days ago does not have this function:
The attacker's financial preparation (From Tornado) was about 6 hours ago, and the identity of the attacker is also worth thinking about.
Summarize
Summarize