event review
event review
On August 10, 2021, PolyNetwork suffered a cross-chain attack, and 600 million U.S. dollars in encrypted assets were transferred (then the attackers began to return the stolen assets one after another). The attacker carried out attack transactions on multiple public chains, and completed the attack through cross-chain management contracts and repeater components.
secondary title
Attack analysis
1. The hacker initialized an attack transaction that should have been invalid on the source chain.
2. The attack transaction was written into the source chain without being fully checked, and then included in the Alliance Chain’s Merkle tree by the repeater and signed, and then released to the Alliance Chain block.
3. The hacker uses the effective Merkle proof of step 2 on the target chain to call the ECCM contract of Poly Network, and changes the keepers to the public key controlled by the hacker.
4. After obtaining the keepers permission, hackers can arbitrarily unlock assets on multiple public chains.
secondary title
detailed analysis
1. The hacker initiated an attack transaction on the source chain at 17:32:32 on August 10, 2021, Beijing time.
https://explorer.ont.io/tx/F771BA610625D5A37B67D30BF2F8829703540C86AD76542802567CAAFFFF280C#
We decoded the transaction and got the following parameter map.
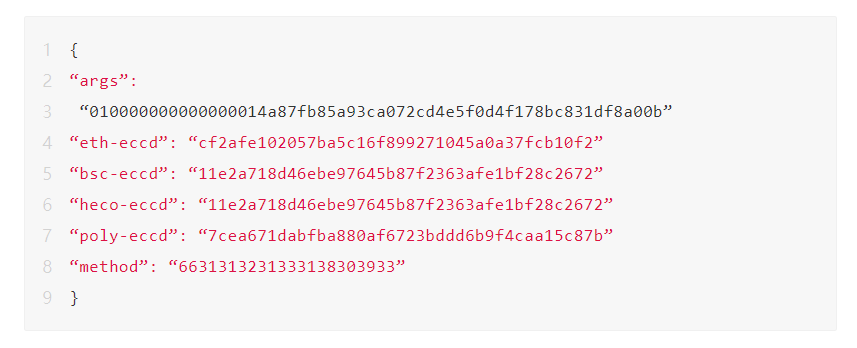
2. This attack transaction calls a method"66313231333138303933", and its corresponding signature is equal to 0x41973cd9 (same as the signature of the putCurEpochConPubKeyBytes function called later). This transaction should be an invalid transaction, but it was written into the source chain and included in the Merkle tree of the Alliance Chain by the repeater, signed, and then published to the Alliance Chain block. Merkle tree is used to prove whether the transaction actually exists. The resulting cross-chain transactions are as follows:
https://explorer.poly.network/tx/1a72a0cf65e4c08bb8aab2c20da0085d7aee3dc69369651e2e08eb798497cc80
3. The cross-chain transaction calls the EthCrossChainManager.verifyHeaderAndExecuteTx() of the Poly Network contract on the target chain. The first parameter contains the Merkle proof. The analysis is as follows:
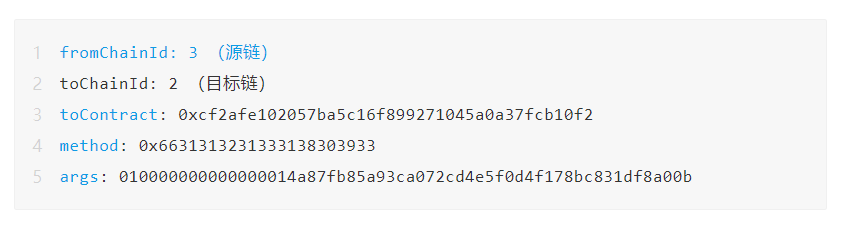
4. This function analyzes the Merkle proof and finds that the proof is valid, and the attack transaction does exist in the signed Merkle tree. Then call the EthCrossChainManager._executeCrossChainTx() function to execute the transaction, that is, call toContract to point to the method (0x6631313231333138303933) in the contract (0xcf2afe102057ba5c16f899271045a0a37fcb10f2), and pass in the parameter args ( 010000000000000014a87fb85a93ca072cd4e5f0d4f178bc831df8a00b). And this method points to putCurEpochConPubKeyBytes(bytes), because its function signature is the same as the method signature mentioned in step 2 (both are 0x41973cd9, here is a hash collision), so it is successfully executed, and the public key of the keepers is changed to a hacker 's public key. Transactions on Ethereum are as follows:
https://etherscan.io/tx/0xb1f70464bd95b774c6ce60fc706eb5f9e35cb5f06e6cfe7c17dcda46ffd59581
secondary title
event summary
This attack is composed of a series of transactions, and the root cause of the attack is analyzed as follows:
1. The attack transaction is written to the source chain without sufficient checks.
2. The repeater will receive any"makeFromOntProof"Event transactions.
3. The repeater publishes the transaction in step 1 to the Alliance Chain.
4. In step 2, the attack transaction is incorporated into the Merkle tree of the Alliance Chain, generating a valid Merkle proof.
5. The ECCM contract on the original chain has passed the Merkle certificate generated in step 2, which verifies that the transaction "really exists" on the source chain, and the original data has not been destroyed or modified. However, it is important to emphasize that transactions should be fully verified before constructing Merkle proofs that will be sent to the target chain. As shown in the design document.
“The management contract fetches the block headers from chain A, verifies whether or not the cross chain parameters and the proof are valid, and then transmits the necessary information to chain B in the form of an event;”
"The management contract obtains the block header from the A chain, verifies whether the cross-chain parameters and proofs are valid, and then transmits the necessary information to the B chain in the form of events;"
Therefore, the target chain (i.e. B-chain) should use Merkle proofs to verify that the received information is uncorrupted and unaltered, and transaction information should be fully verified before being sent to the target chain.
Attachment: Merkle tree (https://en.wikipedia.org/wiki/Merkle_tree) is defined as follows: Hash tree can be used to verify any kind of data stored, processed and transmitted in and between computers. They can help ensure that data blocks received from other peers in the peer-to-peer network are uncorrupted and unaltered, and can even check whether other nodes are lying and sending fake blocks.





