
In recent months, there have been a number of security incidents related to price accuracy calculation vulnerabilities in the contract development process. The amount of losses has exceeded 10 million US dollars, including MIM_SPELLs US$6.5 million, RadiantCapitals US$4.5 million, Onyx Protocols US$2.1 million, etc. Because there is a problem with the accuracy during calculation, key variables are calculated incorrectly and are attacked.
SharkTeam summarized such security incidents and gave effective security suggestions. It is hoped that subsequent protocols can serve as a warning and protect the security of users encrypted assets.
1. MIM_SPELL attack incident
Occurrence: January 30, 2024
Amount of loss: Approximately $6.5 million,
Reason for the vulnerability: There are two lending variables elastic and base in the contract. When calculating the accuracy of the two, they both use the upward rounding method. This operation will cause the parameter that should be calculated to be 0 to be finally calculated to be 1, causing an imbalance between the two parameters, and ultimately being able to over-lend MIM tokens.
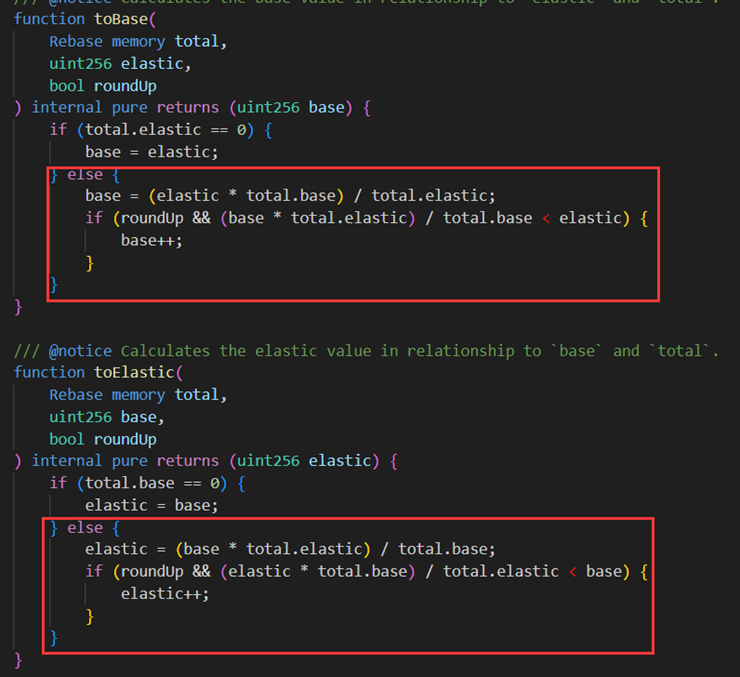
Detailed analysis:https://bit.ly/3ScR7TK
2. RadiantCapital attack incident
Occurrence: January 2, 2024
Amount of loss: Approximately $4.5 million,
Reason for the vulnerability: The hacker took advantage of the vulnerability in the contract that the new market has not been initialized. The liquidity index was not initialized, allowing the hacker to manipulate its size through the flash loan function. When the index became larger, the hacker took advantage of the rounding accuracy in the rayDiv function. The problem is that as the exponent becomes larger, the upper limit of precision loss caused by rounding also becomes larger, and hackers can profit from repeated access operations.
3. Onyx Protocol attack incident
Occurrence: November 11, 2023
Amount of loss: Approximately $2.1 million,
Reason for the vulnerability: Similar to the RadiantCapital attack incident, the vulnerability that the new market has not yet initialized liquidity is also exploited, and there is a rounding vulnerability in the divUint function that causes precision loss.
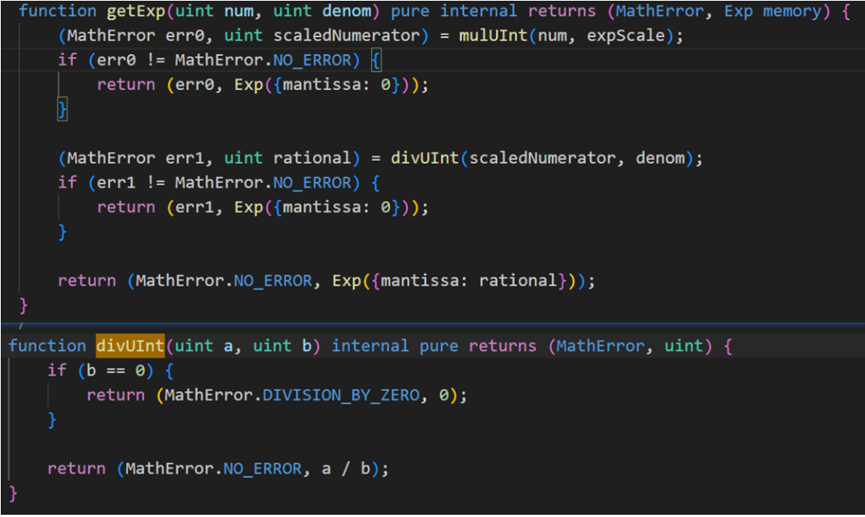
Detailed analysis:https://bit.ly/47cKeI6
4. WiseLending attack incident
Occurrence: January 12, 2024
Amount of loss: Approximately $465,000,
Reason for the vulnerability: The contract uses upward rounding when calculating the loan share. The attacker uses this to perform repeated deposit and withdrawal operations to increase the share price. After the share price increases, he borrows a large amount of ETH with his own share.
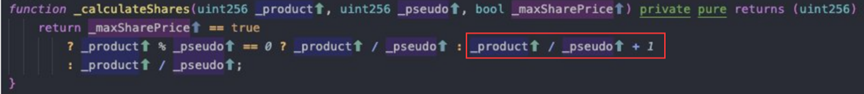
5. HopeLend attack
Occurrence: October 18, 2023
Damage: Approximately $850,000
Reason for the vulnerability: The hacker initially took advantage of the liquidity imbalance in the pool corresponding to the target asset, manipulated the liquidity index of hToken associated with the target asset, and distorted its value. The hackers then borrowed all other underlying assets using a very small amount of hToken collateral. After that, the hacker also exploited the rounding vulnerability in the rayDiv function in the contract split operation to repeatedly deposit and withdraw funds, depleting the underlying assets invested in the Hopelend attack.
Vulnerability summary and security suggestions
Accuracy issues are generally divided into two categories:
1. One type is incorrect upward rounding, which may cause a parameter that should be 0 to be taken as 1, causing serious loopholes in subsequent calculations;
2. The second category is rounding problems, of which the most serious ones are projects that incorrectly use the rayDiv function.
Safety advice:
1. For the first category, if the project logic requires upward rounding, multiple and diverse repeated tests should be performed under conditions such as the rounding variable is 1 or 0, etc.
2. For the second type, you can use the method of multiplying first and dividing with uniform precision, for example, using 10** 18 as the suffix as the value after the decimal point.
3. No matter what the situation is, test the calculation logic in all aspects and consider every situation as much as possible. Especially when different calculation results have different processing logic, careful testing is needed. The theoretical logic design is combined with the actual code implementation to test the contract functions in an all-round way without any blind spots. If test cases can cover various changes, security issues caused by precision calculations can be avoided.
About Us
SharkTeams vision is to secure the Web3 world. The team consists of experienced security professionals and senior researchers from around the world, who are proficient in the underlying theory of blockchain and smart contracts. It provides services including on-chain big data analysis, on-chain risk warning, KYT/AML, smart contract audits, encrypted asset recovery and other services, and has created an on-chain intelligent risk identification platform ChainAegis. The platform supports unlimited levels of in-depth graph analysis and can effectively Fight against the Advanced Persistent Threat (APT) in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, Collab.Land, etc.
Official website:https://www.sharkteam.org
Twitter:https://twitter.com/sharkteamorg
Discord:https://discord.gg/jGH9xXCjDZ
Telegram:https://t.me/sharkteamorg





