This article comes fromThis article comes from, Original Author: Chainalysis Team
Odaily Translator | Nian Yin Si Tang

Odaily Translator | Nian Yin Si Tang
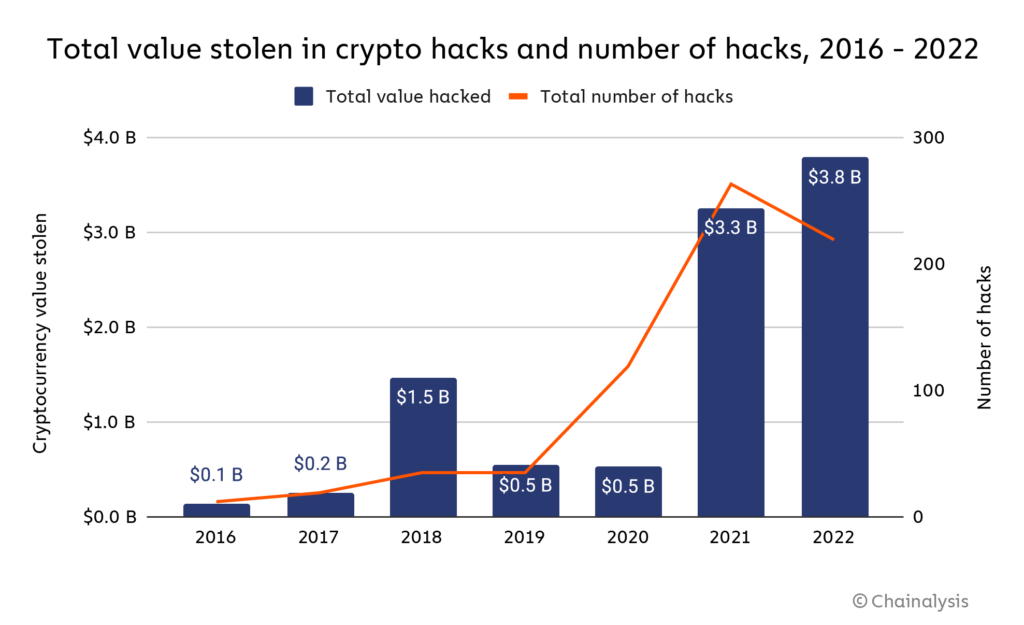 2022 will be the largest year for hacking in the history of the cryptocurrency industry, with a total of $3.8 billion stolen in the field.
2022 will be the largest year for hacking in the history of the cryptocurrency industry, with a total of $3.8 billion stolen in the field.
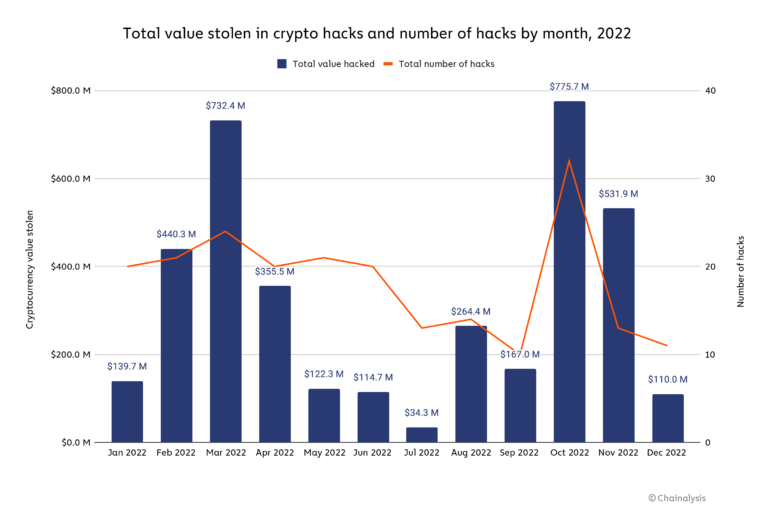 Below, we take a deep dive into which types of platforms are most affected by hackers, and look at the role played by North Korea-linked hackers, who are driving the majority of cryptocurrency hacking in 2022 and breaking their own charts for stealing the most cryptocurrency. annual record.
Below, we take a deep dive into which types of platforms are most affected by hackers, and look at the role played by North Korea-linked hackers, who are driving the majority of cryptocurrency hacking in 2022 and breaking their own charts for stealing the most cryptocurrency. annual record.
secondary title
DeFi Protocols Are the Biggest Victims of Cryptocurrency Hacks
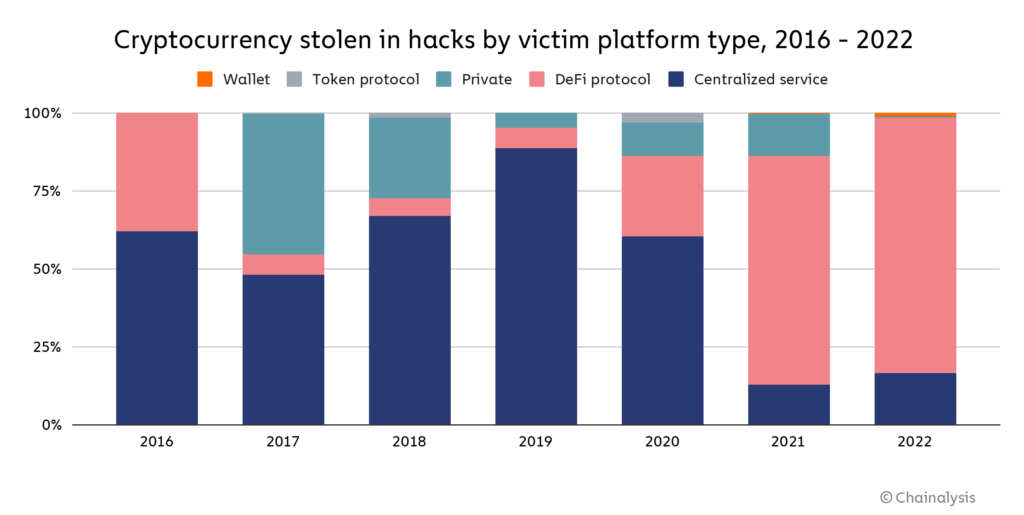 Of all cryptocurrencies stolen by hackers, DeFi protocols accounted for 82.1% of the victims, with a total of $3.1 billion stolen, up from 73.3% in 2021. Of that $3.1 billion, 64% came from cross-chain bridge protocols. A cross-chain bridge is a protocol that allows users to transfer cryptocurrencies from one blockchain to another, usually by locking the user's assets in a smart contract on the original chain, and then on the second chain Generate an equal amount of assets. Cross-chain bridges are an attractive target for hackers, because the smart contract effectively becomes a giant, centralized repository of funds backing assets that have been bridged to the new chain—a much more complex transaction beyond imagination. Ideal honeypot. If the bridge gets big enough, any bugs or other potential weaknesses in its underlying smart contract code will almost certainly end up being discovered and exploited by bad actors.
Of all cryptocurrencies stolen by hackers, DeFi protocols accounted for 82.1% of the victims, with a total of $3.1 billion stolen, up from 73.3% in 2021. Of that $3.1 billion, 64% came from cross-chain bridge protocols. A cross-chain bridge is a protocol that allows users to transfer cryptocurrencies from one blockchain to another, usually by locking the user's assets in a smart contract on the original chain, and then on the second chain Generate an equal amount of assets. Cross-chain bridges are an attractive target for hackers, because the smart contract effectively becomes a giant, centralized repository of funds backing assets that have been bridged to the new chain—a much more complex transaction beyond imagination. Ideal honeypot. If the bridge gets big enough, any bugs or other potential weaknesses in its underlying smart contract code will almost certainly end up being discovered and exploited by bad actors.
secondary title
How can we make DeFi safer?
DeFi is one of the fastest-growing and most compelling areas of the cryptocurrency ecosystem, largely because of its transparency. All transactions happen on-chain, and the smart contract code governing DeFi protocols is publicly visible by default, so users know exactly what happens to their funds when they are spent. This is especially attractive in 2023, as many of the crypto market crashes of the past year have been due to a lack of transparency into the actions and risk profiles of centralized cryptocurrency businesses. But that same transparency also makes DeFi so vulnerable — hackers can scan the DeFi code for vulnerabilities and attack at the perfect time to maximize the theft of user assets.
DeFi code audits performed by third-party providers are one possible remedy. One such provider is blockchain cybersecurity firm Halborn, known for its clean track record — no DeFi protocol that passed Halborn’s audit was subsequently hacked. We caught up with Halborn COO David Schwed, whose background includes working in risk and security at large banks like BNY Mellon, to discuss how DeFi protocols can better protect themselves. He emphasized that many of the problems in DeFi come down to a lack of investment in security. "A large protocol should have a security team of 10 to 15 people, each with a specific area of expertise," he told us. He also pointed out that the core problem is that DeFi developers are prioritizing growth over everything else, and directing funds spent on security measures to provide incentives to attract users. “The DeFi community generally doesn’t ask for better security — they want to use high-yield protocols. But these incentives end up causing trouble.”
Schwed told us that DeFi developers should learn from traditional financial institutions on how to make their platforms more secure. "You don't need to be as slow as a bank, but there are some things you can learn from them." Among the steps he recommends are:
- Test protocols with simulated attacks. DeFi developers can simulate different hacking scenarios on testnets to test how their protocols handle the most common attack vectors.
- Leverage the transparency of cryptocurrencies. A huge advantage of a blockchain like Ethereum is that transactions are visible in the mempool until they are confirmed on the blockchain. Schwed recommends that DeFi developers closely monitor mempools for suspicious activity on smart contracts, allowing for early detection of possible attacks.
Schwed also told us that regulators have a role to play here and can help improve DeFi security by setting minimum security standards that protocol developers must adhere to. The data on DeFi hacks shows one thing: Whether through regulation or voluntary adoption, DeFi protocols would greatly benefit from adopting better security to facilitate ecosystem growth, prosperity, and eventually mainstream penetration.
secondary title
North Korea-linked hackers break record again: $1.7 billion stolen
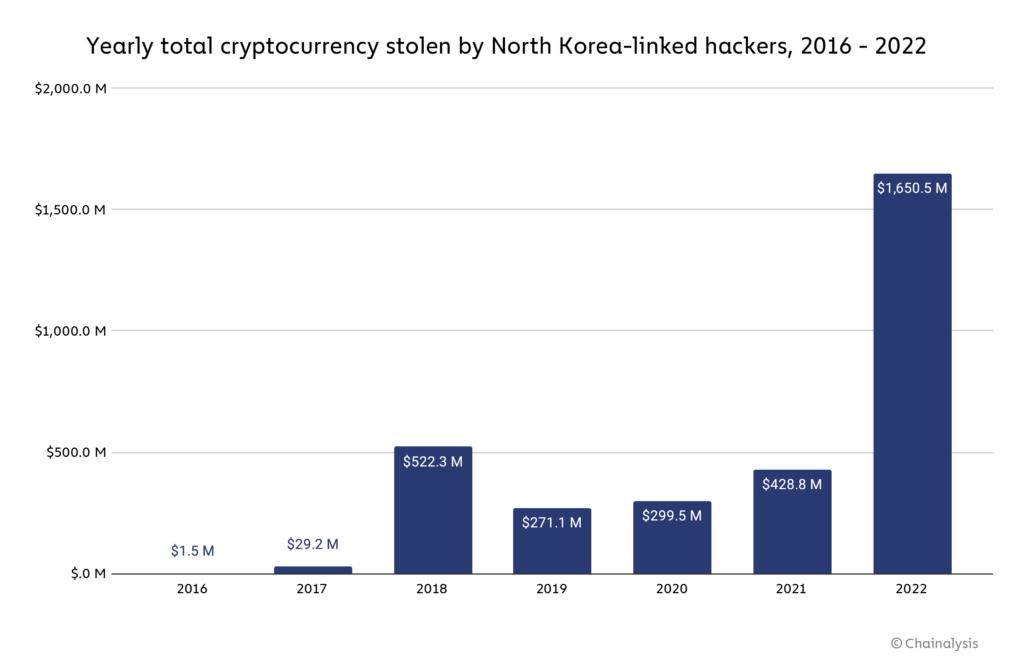 North Korea-linked hackers, such as those of the cybercriminal group Lazarus Group, have been the most prolific cryptocurrency hackers in recent years. In 2022, they broke their own theft record, we believe they stole about $1.7 billion worth of cryptocurrency in several hacks. It’s worth mentioning that North Korea’s merchandise exports totaled $142 million in 2020, so it’s not an exaggeration to say that cryptocurrency hacks are the source of a large portion of the country’s economy.
North Korea-linked hackers, such as those of the cybercriminal group Lazarus Group, have been the most prolific cryptocurrency hackers in recent years. In 2022, they broke their own theft record, we believe they stole about $1.7 billion worth of cryptocurrency in several hacks. It’s worth mentioning that North Korea’s merchandise exports totaled $142 million in 2020, so it’s not an exaggeration to say that cryptocurrency hacks are the source of a large portion of the country’s economy.
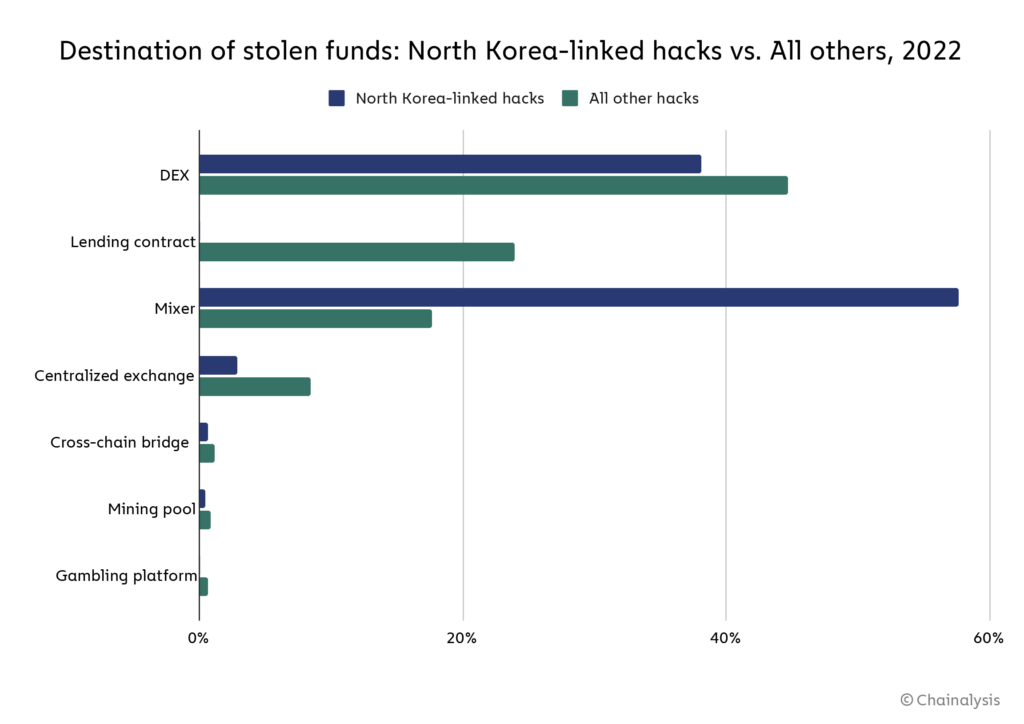 In addition to DeFi protocols, North Korea-linked hackers also tend to send large sums of money to mixers, which is often the cornerstone of their money laundering process. In fact, funds from hacks by North Korean-linked hackers are transferred to mixers much faster than funds stolen by other individuals or groups. But what kind of mixer are they using? We will continue to discuss next.
In addition to DeFi protocols, North Korea-linked hackers also tend to send large sums of money to mixers, which is often the cornerstone of their money laundering process. In fact, funds from hacks by North Korean-linked hackers are transferred to mixers much faster than funds stolen by other individuals or groups. But what kind of mixer are they using? We will continue to discuss next.
secondary title
New Mixer Used by North Korean Hackers After Tornado Cash Is Targeted by US OFAC
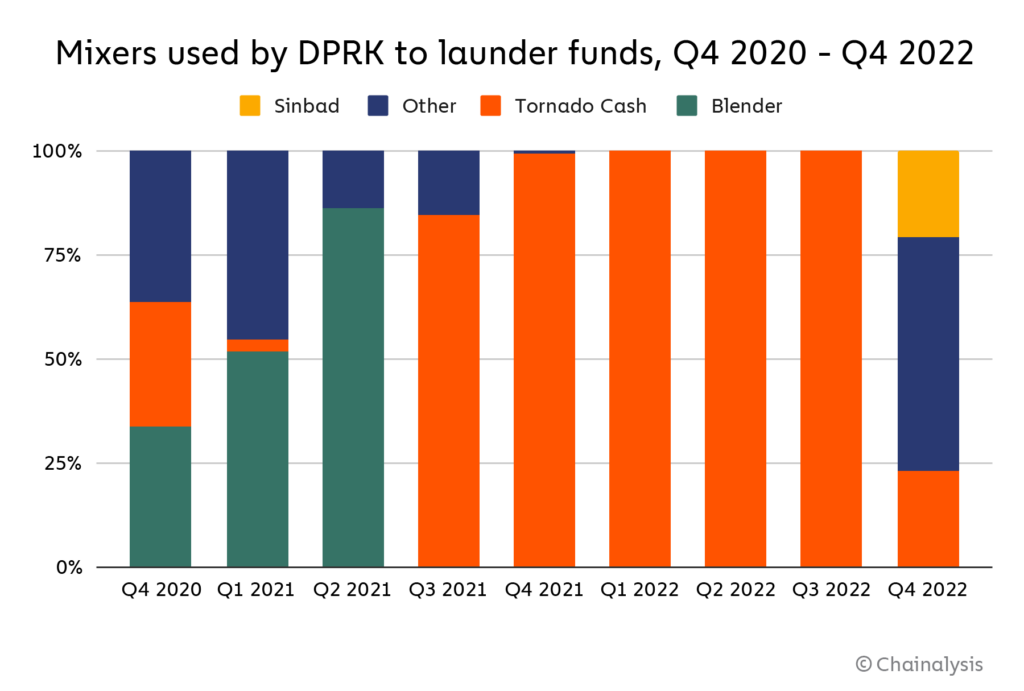 However, when Tornado Cash was sanctioned in August 2022, the hackers adjusted. While North Korea-linked hackers have still sent some funds to Tornado Cash since then, we can see above that they diversified their use of mixers in Q4 2022, shortly after the mixers were designated. This may be because, while Tornado Cash is still running, its total transaction volume has declined since being sanctioned, and mixers generally become less effective when fewer people use them. Since then, the hackers have turned to another mixer, Sinbad, which we detail below.
However, when Tornado Cash was sanctioned in August 2022, the hackers adjusted. While North Korea-linked hackers have still sent some funds to Tornado Cash since then, we can see above that they diversified their use of mixers in Q4 2022, shortly after the mixers were designated. This may be because, while Tornado Cash is still running, its total transaction volume has declined since being sanctioned, and mixers generally become less effective when fewer people use them. Since then, the hackers have turned to another mixer, Sinbad, which we detail below.
Sinbad
secondary title
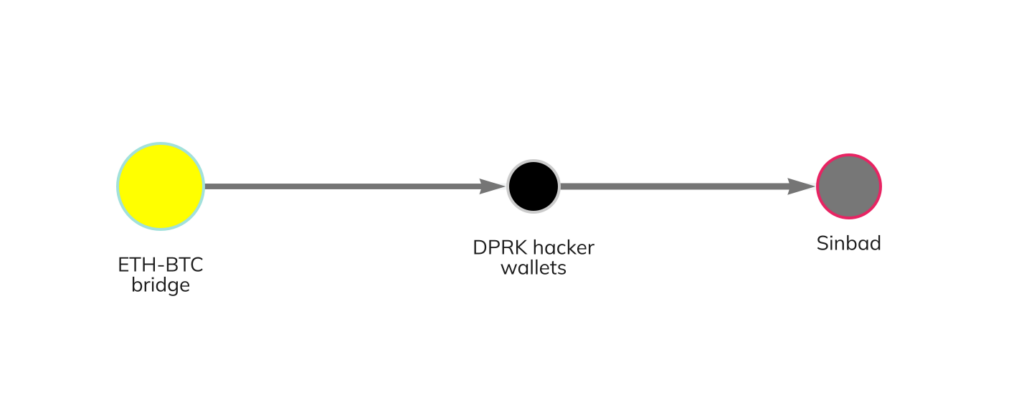 Sinbad is a relatively new hosted bitcoin mixer that began advertising its services on the BitcoinTalk forum in October 2022. Chainalysis investigators first discovered wallets belonging to North Korea-linked hackers sending funds to the service in December 2022, see Chainalysis Reactor’s chart below.
Sinbad is a relatively new hosted bitcoin mixer that began advertising its services on the BitcoinTalk forum in October 2022. Chainalysis investigators first discovered wallets belonging to North Korea-linked hackers sending funds to the service in December 2022, see Chainalysis Reactor’s chart below.
As we have seen in many North Korean-directed hacks, the hackers bridged the stolen funds of the Ethereum blockchain (including some of the funds stolen in the Axie Infinity attack) to Bitcoin, and then sent the Bitcoin to Sinbad. Between December 2022 and January 2023, North Korea-linked hackers sent a total of 1,429.6 bitcoins, worth about $24.2 million, to the mixer.