Summary
first level title
Summary
SBT was proposed by Vitalik in a paper inspired by the game "World of Warcraft". It is a publicly visible, non-transferable, but withdrawable token type. The account bound to these SBTs is the soul, which can correspond to individuals, institutions, organizations, etc., and one soul can have multiple SBTs. SBT marks the user's characteristics and achievements on the chain in the form of tokens, with verifiable information. SBT can help users build native digital identities in the web3.0 world, and finally realize the vision of a decentralized society. The concepts of SBT and DID overlap. From a functional point of view, they both hope to describe the characteristics of users in the form of certificates or identifiers, and then construct a digital identity. SBT is a bottom-up solution, a means to achieve decentralized identity.
The SBT track is still in its early days, and it mainly faces the problems of no unified technical standards, difficulty in balancing privacy protection and verifiability, and loopholes in some application scenarios. After it has accumulated a certain foundation, some new use cases may appear, such as cross-platform SBT to allow users to operate more freely, refined SBT to make marketing more accurate and SBT-based credit lending.
first level title
1. Dependent origin: the past and present of SBT
secondary title
1.1 Etymology and meaning
With the popularity of the NFT market, NFT is widely used in the confirmation of scarce digital assets due to its unique and indivisible characteristics, and its form also fits well with the scarce props in the game. Not only that, but it also has some other functions, such as being used as a proof of a certain ability, qualification or social status. However, since NFT can be transferred freely, especially in the past two years, there have been many wealth-making stories about NFT, which has caused people to pay too much attention to its transaction attributes. At this time, if NFT is still used as a certificate of a medal or ability, then it is impossible to judge whether the holder really has this qualification or just has enough wealth. Therefore, Vitalik got inspiration from the soul binding mechanism and tried to combine the two to open up some new application scenarios.
In the article "Decentralized Society: Finding Web3's Soul", Vitalik elaborated his idea and gave a clear definition of soulbound token (SBT, soulbound token). SBTs are publicly visible, non-transferable, but withdrawable NFTs. This NFT represents a certain behavior or experience that the user has had on the chain. Since these actions take place on the blockchain, they are inherently traceable. The relevant accounts bound to these SBTs are souls, which can correspond to individuals, institutions, organizations, etc., and one soul can have multiple SBTs. Not only that, SBT is often used to form commitments, certificates or affiliations of social relationships in the web3 world, which acts like an extensible resume, which will correspond to the characteristics and achievements of the soul in tokens on the blockchain. Forms are tagged with verifiable information. As a result, SBT can help users build a native digital identity that mirrors the real society in the web3.0 world, and finally realize the vision of a decentralized society by establishing and expanding this social network.
secondary title
1.2 New solutions for decentralized identity
Careful readers may have doubts. SBT seems to be very similar to the existing DID track, and they think that SBT is a replica of DID. Admittedly, the two tracks are closely related, and there are many crossovers between the concepts. Therefore, it is necessary for us to clarify the difference between the two, and explain their respective values and development paths.
The full name of DID is Decentralized Identifier, Decentralized Identifier, which emphasizes decentralization and hopes that users can have complete control over their own identities, rather than being controlled by large centralized platforms in the web2 world. This is also the core narrative of previous DID projects.
As for "ID", people have different understandings, which have dual meanings of "symbol" and "identity". The standard concept of DID was proposed and explained in the working draft on DID published by W 3 C in 2019. Later, in 2021, the "Recommended Standards for Publishing Decentralized Identifiers (DIDs) Version 1.0 Proposals" was released, explaining the meaning of DID in detail. It says "Entities are identified by a decentralized identifier and can be authenticated by proof (e.g., digital signatures, privacy-preserving biometric protocols, etc.)." From here, it can be seen that a DID is used to identify an entity symbol. What this symbol can be used to identify is not clearly defined in the standard.
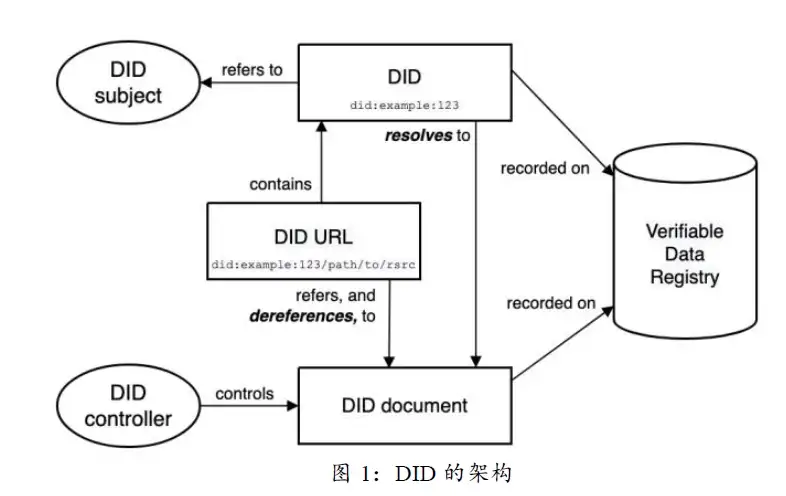
The emergence of DID is to change the current status quo that digital identities are controlled by central institutions. It aims to return the ownership of digital identity data to users while building a global digital identity. Just like the ID number in real life, each person has only one and cannot be transferred, and all other certificates can be associated with it. Therefore, some people are more inclined to interpret DID as Decentralized Identity, a global identity that includes various characteristics of users.
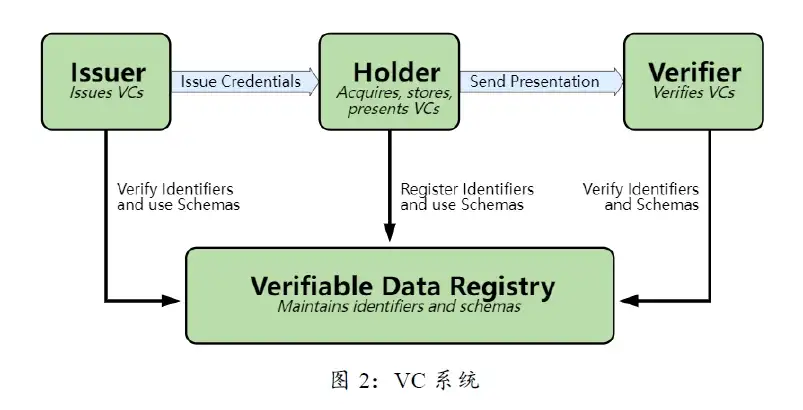 From an architectural point of view, the DID system roughly includes decentralized identifiers and DID documents, DID parsers, verifiable credentials (VC), verifiable data registry and other components.
From an architectural point of view, the DID system roughly includes decentralized identifiers and DID documents, DID parsers, verifiable credentials (VC), verifiable data registry and other components.
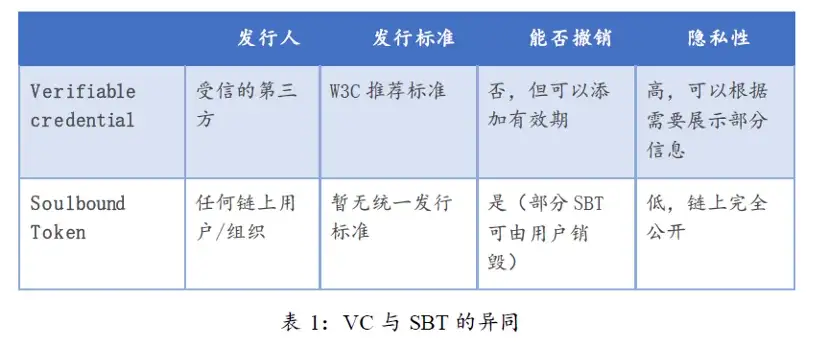 In a series of W 3 C recommendations, DID uses verifiable credentials (Verifiable Credential, VC) as a means of verification. VC is generated by a third party (Issuer) to prove that the user has certain attributes. For privacy protection, the user's identity information is usually stored off-chain, and the Issuer has the right to access the data, generate a zero-knowledge proof and upload it to the chain. This enables the user's identity to be proven without revealing privacy. Users can reuse VC in their wallets, just like holding other encrypted assets.
In a series of W 3 C recommendations, DID uses verifiable credentials (Verifiable Credential, VC) as a means of verification. VC is generated by a third party (Issuer) to prove that the user has certain attributes. For privacy protection, the user's identity information is usually stored off-chain, and the Issuer has the right to access the data, generate a zero-knowledge proof and upload it to the chain. This enables the user's identity to be proven without revealing privacy. Users can reuse VC in their wallets, just like holding other encrypted assets.
From this point of view, although both VC and SBT are DID solutions, they are slightly different. The characteristics of VC and SBT are summarized in the table below.
I believe that everyone will understand after seeing this. The confusing part is that DID has double meanings. When the DID project uses some kind of identifier to represent a general certificate, especially when this certificate cannot be transferred, it has the same function as that implemented by SBT. And when DID is used to represent identity, it is itself the soul bound to SBT (the Soul Bound by Tokens).
In the future, the possible ideal state is as follows: each user corresponds to a unique decentralized identity, and there are many non-transferable credentials under this identity, which respectively represent the user's experience, skills and qualifications in different fields. This identity can be an address or a collection of multiple addresses.
As a result, the industry competition pattern of credentials and identities is naturally clear. Any organization can issue credentials to users. The threshold for this business is low, but several large and influential organizations are required to aggregate credentials into an identity that can be used across multiple applications or even multiple networks. The value of this business is great, and the threshold is relatively high.
first level title
2. Typical SBT-based application
Vitalik’s paper lists 8 SBT-based use cases, such as reputation provision, SBT community recovery, soul airdrop, soul governance, and soul lending. Therefore, this article will not go into details, and here is just a classification of his ideas:
1. Use SBT as a certificate to establish identity;
3. Use SBT as a carrier for non-transferable special assets.
At present, the first two types of applications have appeared on the market. Let's take a look at the role of SBT and its identity based on typical projects.
secondary title
2.1 Certificate class
Due to the non-transferable characteristics of SBT, it is very suitable for expressing the holder's ability and qualifications obtained by his own behavior, rather than the characteristics brought by assets. At present, it seems that certificate-based projects are the most used in SBT-based applications. Such projects are represented by POAP, Project Galaxy, and RabbitHole. What they have in common is that they will issue certificates in the form of SBT for users' on-chain/off-chain behaviors. This credential represents the user's experience or qualifications. Projects that work with it can rely on the credentials users have to more precisely target and filter users for other campaigns or businesses. The following takes RabbitHole as an example to illustrate the typical operation mode of such projects. (Certificates for individual projects are transferable NFTs, but they are designed in the same way.)
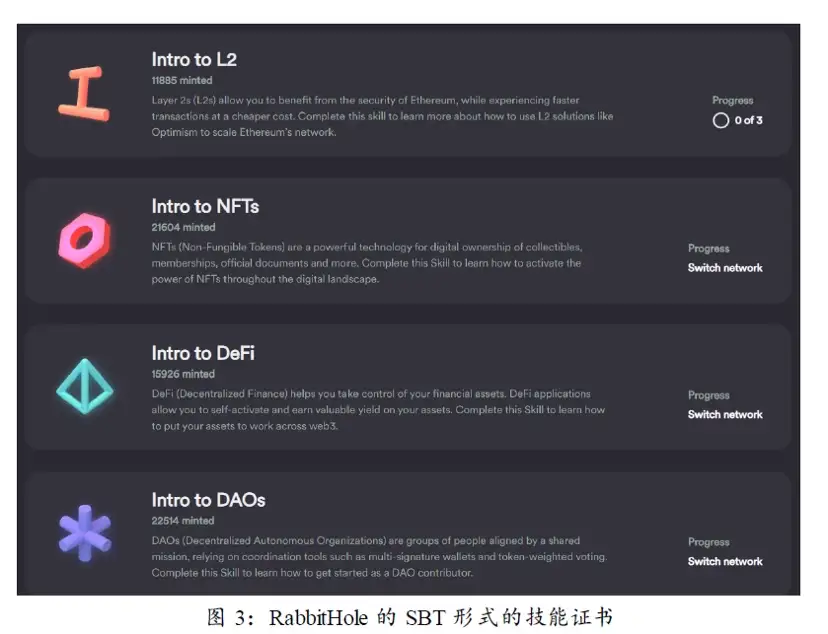 RabbitHole is an award-winning beginner's class. It attracts users by publishing rewarding tasks, allowing users to learn and use specific Web3 applications to receive rewards. Rewards include NFT customized for the event and token rewards provided by the project party.
RabbitHole is an award-winning beginner's class. It attracts users by publishing rewarding tasks, allowing users to learn and use specific Web3 applications to receive rewards. Rewards include NFT customized for the event and token rewards provided by the project party.
In order to be eligible to participate in rewarding activities, users first need to complete basic skills learning and certification in RabbitHole's Skills training camp, and obtain a skill certificate in the form of SBT. For example, in order to obtain an Intro to L2 certificate, users need to complete 3 small tasks, namely, use the Hop cross-chain bridge to transfer ETH to the Optimism network, convert ETH to OP on Uniswap, and mint an NFT on Quix.
After obtaining the skill certificate, users can use this as a prerequisite to participate in more rewarding tasks. For example, Uniswap has cooperated with RabbitHole before and released the Learn L2s with Uniswap task Quest. The prerequisite for completing this task is to have Bright ID certification (real person certification) and the Intro to DeFi certificate issued by RabbitHole itself (there was no Intro to L2 certificate at the time). Quest is divided into 4 small tasks, which are mainly to provide liquidity and transactions in Uniswap deployed on Arbitrum and Optimism. After completing these 4 small tasks, users can get 2 UNI token rewards and an NFT.
We still take RabbitHole as an example. They will operate the entire event together with cooperative projects, including event start and end times, task settings, rewards and expected number of participants settings, community and media promotion, tutorial production, etc. RabbitHole will charge 20% of the event reward amount as a service fee from partners, and lock it for 1 year. From this point of view, this service fee is more like an operating fee, and the data usage fee is only a part of it.
The key point of certificate projects is to have partners recognize their certificates and carry out activities based on the certificates. On the one hand, their income is more dependent on the overall activity of the market. When the market is active and various projects can provide funds for customer acquisition, their income is guaranteed. And when the market is quiet, they don't have much business to do. On the other hand, their income depends on their market influence. If a project has been running for a long time, has a large and active community, and can attract users' attention, their certificates are more likely to be recognized and have practical effects.
secondary title
2.2 Identity class

SBT-based identity projects use SBT directly as the user's identity credentials. In this system, SBT realizes the function of DID. Representatives of identity projects include BAB and the Palau Digital ID mentioned at the beginning.
BAB is the first soul-bound token based on BNB Chain launched by the exchange Binance in September 2022. It is the concrete implementation of the SBT concept on the identity proof track. BAB is bound to a Binance account and follows the ERC-721 standard. Only users who have undergone KYC on the trading platform can apply, and a single account ID can only mint one, and the minting fee is 1 BUSD. Once minted, BABs are non-transferable, only revocable.
Although BAB was born not long ago, its actual landing has also brought some foreseeable opportunities.
(1) For holders, although the non-transferable nature of BAB makes it have no direct financial and wealth value, it represents the on-chain behavior certificate corresponding to the address and can be verified by others. The user only needs to hold it to prove that he has successfully passed Binance’s KYC process, which can effectively avoid being included in the robot account and miss out on potential airdrop rewards.
(2) For Binance, it can not only earn a certain amount of income on the chain by providing channels for casting BAB, but also verify the time when a user minted BAB to judge the loyalty of the user, and even analyze the BAB in the future. Holders' on-chain behaviors to provide precise services.
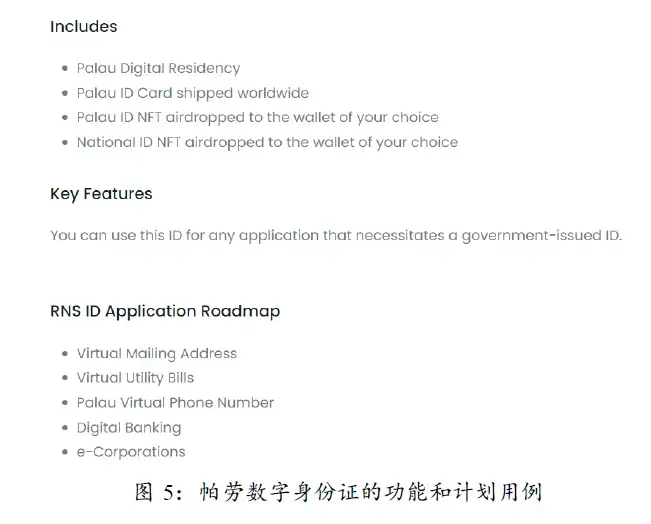 Palau's digital ID is also an identity-like SBT. Applying to rent (US$ 248 for one year) this SBT needs to go through KYC procedures, including uploading ID photo, profile picture, filling in height and weight, etc. Its planned use cases include address verification, KYC verification, access to digital banks, legally verified chain signatures, digital company registry services, and other potential products such as asset ownership and insurance. The official also specifically stated that it can be used in any application that requires a government-issued ID.
Palau's digital ID is also an identity-like SBT. Applying to rent (US$ 248 for one year) this SBT needs to go through KYC procedures, including uploading ID photo, profile picture, filling in height and weight, etc. Its planned use cases include address verification, KYC verification, access to digital banks, legally verified chain signatures, digital company registry services, and other potential products such as asset ownership and insurance. The official also specifically stated that it can be used in any application that requires a government-issued ID.
An identity project can be regarded as a high-level project that aggregates multiple certificates issued by itself. BAB itself is an identity, which contains a user's Binance KYC "certificate", and may contain more information such as interaction and holding information on the BNB Chain in the future. The KYC certificate is the link between real users and the cyber world. General blockchain projects are unable to issue it to users, and only exchanges, asset management companies, etc. will issue it. Well-known exchanges have a large traffic advantage, so they have become the first choice for issuing SBT-based identities. In the future, several large exchanges may combine with their own closely related public chains to issue identities on the chains. This will effectively reduce the interference of robot users on encrypted applications, and allow ordinary users to obtain a more comfortable on-chain experience. If the identity on the chain issued by an exchange can achieve a large-scale consensus, or even a consensus across several public chains, this SBT will attract incremental users and resources for the exchange and realize feedback.
secondary title
2.3 Semi-credit lending category
Since the summer of DeFi in 2020, lending projects have developed rapidly, but most of them are mortgage lending projects. Mortgage lending conforms to the characteristics of no permission and no threshold in the encrypted world, but it has inherent shortcomings in the efficiency of capital utilization. Credit lending projects such as TrueFi, Goldfinch, and Maple emerged later. They provided credit loans to encrypted companies that have passed off-chain KYC, expanded the market size of lending, and improved the efficiency of institutional traders and encrypted companies’ use of funds. However, it is still difficult for ordinary users to obtain loans with credit. One reason is the lack of identity and credit certification on the chain, making it difficult for lenders to measure the credit risk of borrowers. That's why Vitalik proposed the concept of "soul loan" in his paper, hoping that SBT can be used as a historical record of credit to prove that users have a good reputation, so that they can directly obtain loans without collateral.
At present, there is no project in the industry that fully uses SBT as a basis to provide credit loans to general users. However, there have been semi-credit lending projects that judge the user's credit risk level based on the user's behavior and adjust his maximum loan-to-value ratio (loan-to-value, LTV) accordingly. We classify such projects as the second largest category of SBT-based application scenarios. The following uses ARCx as a typical representative to introduce how SBT promotes the operation of such projects.
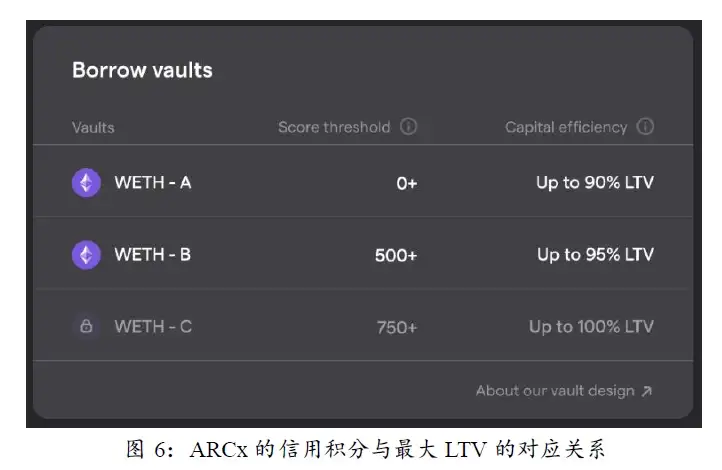
First of all, it needs to be explained that in the official documentation of ARCx, the word "SBT" does not appear clearly, but its approach is similar to SBT, so this article regards it as an SBT project.
The credit score of ARCx is calculated based on the interaction records of the user's address on the chain (Polygon and Ethereum) and the lending agreement, and the calculation formula is completely open. Credit score consists of 3 major items, namely daily score reward, survival score reward and liquidation score penalty. The daily score reward is to reward users who use the ARCx platform within 120 days, and the reward coefficient is calculated based on the user's borrowing utilization rate (the ratio of actual loan LTV to the maximum LTV). According to ARCx’s research on Compound, the loan utilization rate of the most experienced and capable users is mostly around 60%, and they will obtain a reasonable maximum capital utilization efficiency on the basis of risk control. So when ARCx users' borrowing utilization rate is at 60%, they will get more points, and deviating from this ratio, whether it is higher or lower, the growth rate of points will decrease. Both the Survival Score reward and the Liquidation Score penalty measure how much a user is at risk of being liquidated, both of which examine a user's performance across all lending protocols. If there are a large number of liquidation events in the lending market, but the user avoids being liquidated, it means that the user has outstanding risk control ability and should be given a higher score. And if the market is very stable, ordinary users will not be liquidated, and they will not get a high score at this time. Penalties are better understood. If a user has been liquidated within 120 days, 250 points will be deducted directly. The total score is only 999 points. If it is liquidated once in a short period of time, it will not be able to use the pool with the highest borrowing utilization rate of ARCx.
Semi-credit lending projects like ARCx are actually still operating within the safe range of mortgage lending. They measure the user's credit risk by describing the user's credit SBT, and use this to provide more capital-efficient services for users with good credit. At present, it seems that this design is in line with the development status of the encryption industry and is an effective supplement to traditional over-collateralized lending.
3. The development problems of the current SBT track
Although various SBT projects have sprung up after Vitalik's paper, they still have some development difficulties that hinder their further market acceptance.
secondary title
3.1 There is no unified technical standard
Issuing tokens on Ethereum is essentially realized by establishing a new smart contract ledger under a certain address, which records all transaction records of all users interacting with it. This issuance method has formed several unified standards, such as ERC-20 and ERC-721. Developers only need to follow the rules step by step to construct new encrypted tokens of the corresponding type.
The solution to this problem is relatively easy. We need a unified SBT technical standard with public consensus, so as to lay a solid foundation for the application of SBT.
In addition, SBT is also programmable, and it is very hopeful that it will be combined with dynamic NFT in the future, and the oracle machine will be introduced for dynamic update of attributes. Of course, this needs to be included in its unified technical standards.
3.2 It is difficult to balance privacy protection and verifiability
For SBT, it is difficult to balance and balance privacy protection and verifiability. On the one hand, SBT is generated based on the user's on-chain behavior, which is inherently verifiable. It is precisely because it is verifiable that it has credibility. But on the one hand, SBT is equivalent to summarizing the relatively scattered behavior of users and putting a label on it. This increases the risk of user privacy exposure, and on-chain analysis tools can easily grasp user behavior habits. Especially those projects that require KYC certification will face a dilemma. If the user's KYC information cannot be verified by a third party, their SBT will more or less lack credibility, thereby limiting the scope of use. However, if other entities are allowed to verify the user's KYC information, it will inevitably cause information leakage, such as leakage of user information in real life, and cause unnecessary troubles. Of course, this will also affect the brand reputation of this project and the SBT it issues. cause loss. Therefore, on the premise of ensuring user privacy, how to obtain as authentic user data as possible to construct a high-consensus certificate is a big challenge for every SBT project. In the future, technologies such as zero-knowledge proof and multi-party secure computing (MPC) may be used to balance privacy and verification to solve this problem.
3.3 Vulnerabilities exist in some application scenarios
Take the use of SBT for more democratic governance as an example. The token voting mechanism that current DAOs rely on often suffers from Sybil attacks and vote manipulation. The emergence of SBT can help the community effectively screen out fake robot accounts and members outside the community, and alleviate the problem of unfair voting during DAO governance. However, the problem mapping that exists in real life voting also works in the blockchain world, such as bribery. With SBT, those souls with high voting weight are more likely to be discovered by interested people. Once a bribery incident occurs, it is obviously contrary to the original intention of SBT to help achieve fair governance in the community. This one is trickier, and it has moved beyond the realm of computer science and into the realm of sociology.
4. Looking Ahead: Potential Use Cases for SBT
At present, the track of SBT and identity on the chain is in the early stage, and more projects are focusing on how to issue SBT. Assuming we have a more unified technical standard that can make full use of information while protecting privacy, the role of SBT will not be limited to soul airdrops and governance.
4.1 Cross-platform SBT allows users to operate more freely
Internet applications can now log in across multiple applications based on Google, Facebook, WeChat and other accounts, but if users use some of the same type of APP, they will still be required to fill in the same registration information, or need to go through a process of proving their use level. From this perspective, SBT is generated on the blockchain, and the information is publicly available for inspection, which is conducive to cross-application and platform sharing. However, the application range of SBT is still limited to a certain platform at present. If SBT can realize interoperability in the future, it will greatly improve the user experience. For example, a shooting game user wants to choose a favorite game to play for a long time. With the "sharpshooter" SBT issued to him by game A, he can directly go to the master field to compete in game B, eliminating the need for upgrades and Repeated process of accumulating ranked ranks. If he gives up A and chooses B, game B will pay game A a certain customer acquisition fee.
4.2 Refined SBT makes marketing more precise
The current SBT has relatively few dimensions to measure user behavior, and it is relatively shallow, mainly including information such as interacting with an application and obtaining an airdrop. Some projects have already recorded and analyzed deeper user behaviors, and we still need to refine the information of SBT to reflect various information including the amount of user operations, risk preference, time period, and duration of use. Especially when combined with exchange information such as transaction frequency and strategy preferences, what news users pay attention to in the media, etc., the soul depicted by SBT will be closer to the real appearance of users. Based on more refined user portraits, various projects will carry out more precise marketing activities to find the most suitable potential users at a lower cost.
secondary title
3. The content of the report is for reference only, and the conclusions and opinions in the report do not constitute any investment advice on relevant digital assets. Huobi Blockchain Research Institute is not responsible for any losses caused by the use of the content of this report, unless it is clearly stipulated by laws and regulations. Readers should not make investment decisions solely based on this report, nor should they lose the ability to make independent judgments based on this report.
References
1. https://papers.ssrn.com/sol3/papers.cfm? abstract_id= 4105763
2. https://vitalik.ca/general/2022/01/26/soulbound.html
3. https://docs.rabbithole.gg/rabbithole-docs
4. https://wiki.arcx.money/welcome/arcx-credit-introduction
5. https://www.163.com/dy/article/FVJK 69830511 WPT 2.html
6. https://www.w 3.org/TR/vc-data-model/
About Huobi Research Institute
Huobi Blockchain Application Research Institute (referred to as "Huobi Research Institute") was established in April 2016. Since March 2018, it has been committed to comprehensively expanding research and exploration in various fields of blockchain, with a view to pan-blockchain As the research object, the research objectives are to accelerate the research and development of blockchain technology, promote the application of blockchain industry, and promote the ecological optimization of blockchain industry. The main research contents include industry trends, technical paths, application innovation, Pattern Exploration, etc. In line with the principles of public welfare, rigor, and innovation, Huobi Research Institute will carry out extensive and in-depth cooperation with governments, enterprises, universities and other institutions through various forms, and build a research platform covering the complete industrial chain of the blockchain. Industry professionals provide a solid theoretical foundation and trend judgment to promote the healthy and sustainable development of the entire blockchain industry.
contact us:
Consulting email: research@huobi.com
Official website:https://research.huobi.com/
Twitter: Huobi_Research
https://twitter.com/Huobi_Research
Medium: Huobi Research
https://medium.com/huobi-research
Telegram: Huobi Research
https://t.me/HuobiResearchOfficial
disclaimer
1. Huobi Blockchain Research Institute does not have any relationship with the projects or other third parties involved in this report that affect the objectivity, independence, and impartiality of the report.
2. The materials and data cited in this report are all from compliant channels. The sources of the materials and data are considered reliable by Huobi Blockchain Research Institute, and necessary verifications have been carried out for their authenticity, accuracy and completeness , but Huobi Blockchain Research Institute does not make any guarantees about its authenticity, accuracy or completeness.
3. The content of the report is for reference only, and the conclusions and opinions in the report do not constitute any investment advice on relevant digital assets. Huobi Blockchain Research Institute is not responsible for any losses caused by the use of the content of this report, unless it is clearly stipulated by laws and regulations. Readers should not make investment decisions solely based on this report, nor should they lose the ability to make independent judgments based on this report.
4. The information, opinions and speculations contained in this report only reflect the judgment of the researchers on the date of finalizing this report. In the future, based on industry changes and updates of data information, there is a possibility of updating opinions and judgments.
5. The copyright of this report is only owned by Huobi Blockchain Research Institute. If you want to quote the content of this report, please indicate the source. Please let me know in advance if you need to quote a lot, and use it within the scope of permission. Under no circumstances shall any quotation, abridgement and modification contrary to the original intention be made to this report.





