Original Author: Raxy @Jsquare
foreword
first level title
foreword
There have been serial liquidations in the market recently. I think that the demand side of the following tracks (privacy, credit, decentralized identity and reputation system) may have a growth trend due to the defects exposed by the run frenzy. This article tries to learn from individual projects Give examples of its narrative possibilities. Just a little bit of thinking, please correct me if there are obvious mistakes.
secondary title
1. The giant whale was attacked at a critical moment, reflecting the importance of on-chain privacy requirements for institutional-level holders and users. Privacy may require a framework and ecosystem to provide customized services based on user needs, etc.
Although all accounts in the blockchain are currently represented by a series of complex numbers and addresses, if we continuously track and analyze them, we can still discover the identity behind the account, and there are a large number of data analysis tools on the market to help Let's identify these giant whales.
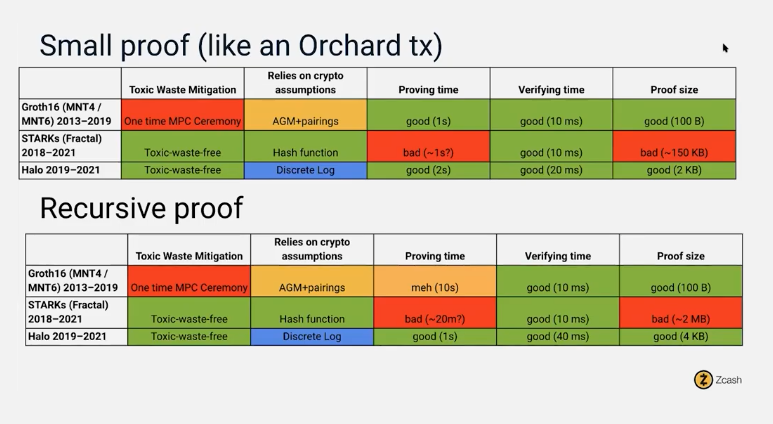
Zero-knowledge proof technology was discovered in the 1980s, but it didn't work or really work for anything until the advent of Zcash in 2016.
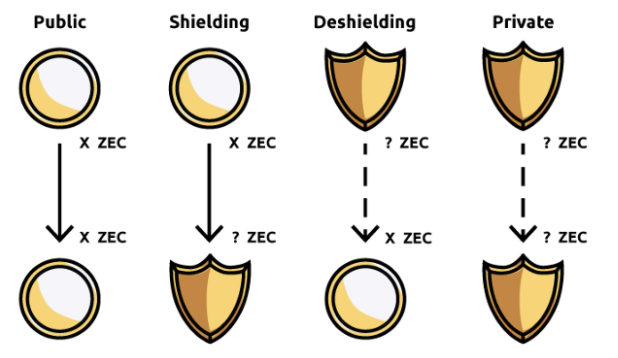
Zcash using Groth16 technology provides two types of addresses: protected privacy addresses (Z) and transparent addresses (T). Z addresses are invisible, and its transactions will not display related addresses, transaction amounts, or encrypted comments. The transparent address (T) can be viewed in a public browser.
And the two address types provided by Zcash can be traded with each other, which creates a process of free choice. You can choose to send assets from Z address to T address to de-anonymize, or you can send them from T to Z address Be anonymous.
image description
The above picture shows the Z and T address conversion process of ZcashBut Zcash has a flaw, everyone uses a specific key to verify the proof, if someone knows the corresponding private key, then they can spoof proofs, so, the master key creates a very important trust problem.Zcash ushered in the discussion of many thinkers at the time, including pressure from anti-money laundering laws.
Therefore, the development so far,
We need to find a clear small panel for privacy requirements
, the dApps on the chain are composed of transactions of varying complexity through users and smart contracts. So any privacy solution must ensure that the two atomic components of the dApp, the user and the smart contract, are both private and secure.Privacy not only needs to solve simple transactions or the anonymity of some behaviors, but also needs to build a larger ecosystem, including different privacy applications to serve users. For example, a giant whale or a market maker may use a variety of strategies to ensure risk exposure during real trading, but none of these behaviors currently meet their privacy needs.
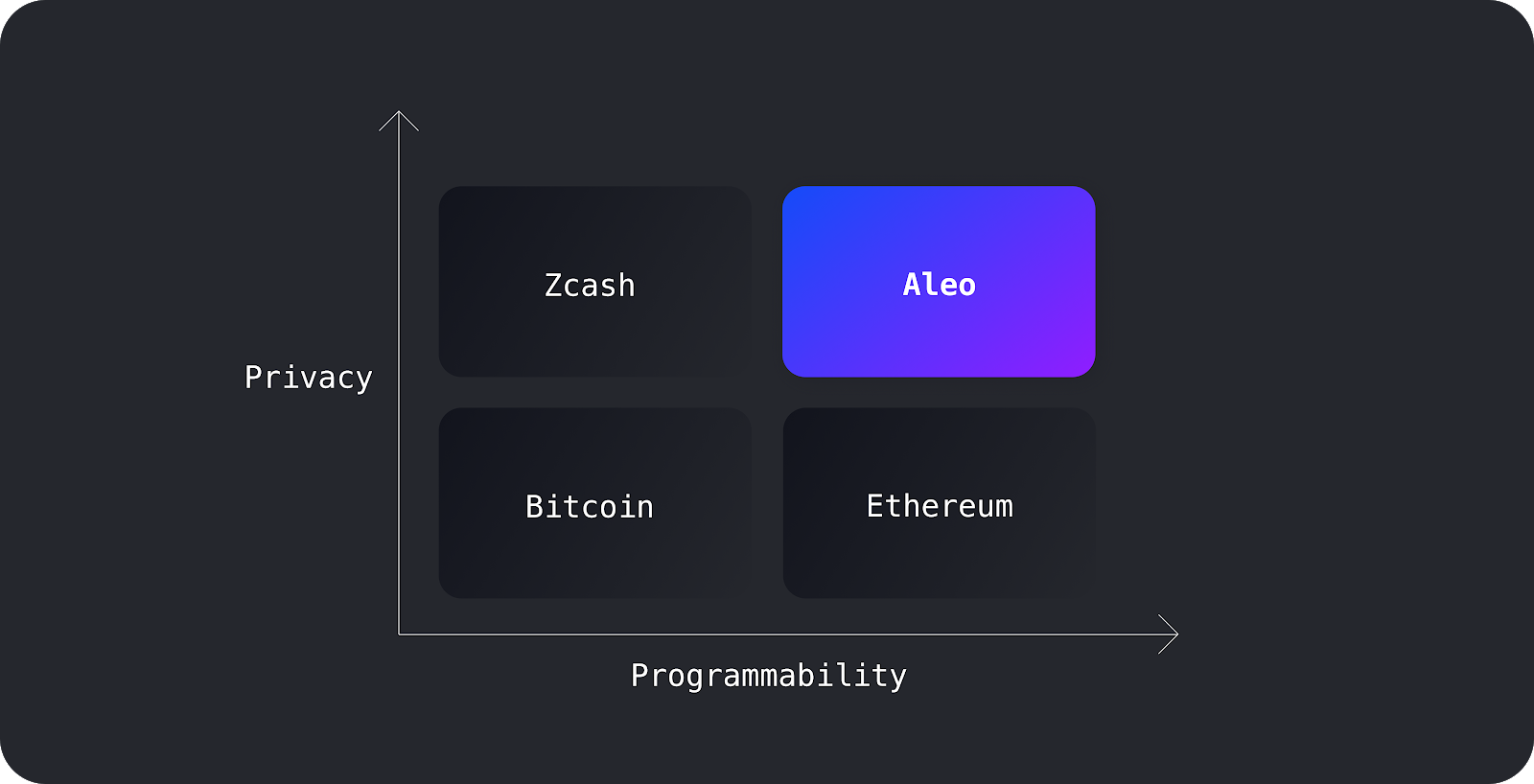
Therefore, privacy requires a large framework and system to develop and create applications based on this framework.
On the basis of Zcash, Aleo not only achieves anonymous asset transfer, but also includes payment, liquidity provision, governance voting, identity authentication and so on.
Only the interacting party knows the details, a malicious third party cannot learn any details or exploit it in any way.
Aleo is a platform for completely private applications, and its core is still ZKP, but Aleo provides a full-stack solution that allows ZK to have programmability at every layer of the stack to achieve large-scale decentralized private calculate. For both users and transactions, the atomic component Aleo can ensure that it does not reveal any identifying information.
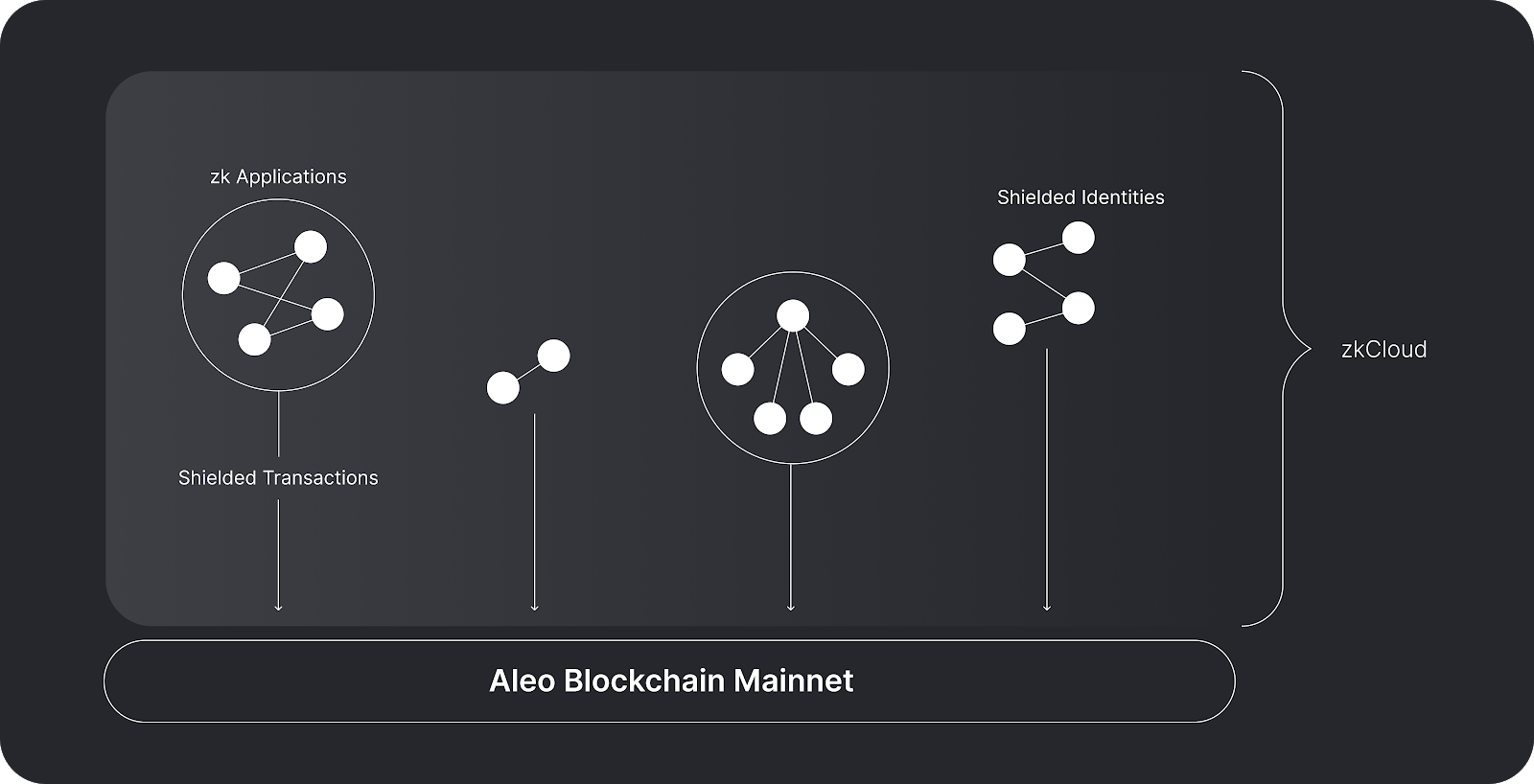
Aleo also supports composable and proprietary applications, and provides a new set of programming language framework "Leo". "Leo" emphasizes readability and ease of use, looks very much like a set of traditional programming language frameworks, abstracts low-level cryptography concepts, and is very friendly to developers.
"zkCloud" enables programmatic interaction between protected identities, be it users, organizations, DAOs, etc. This computational model can be run locally or delegated to dedicated validators.
In addition, Aztec, which also uses ZKP, is also good. Aztec will make up for the privacy needs of Ethereum, and Secret Network, which uses TEE. Since the adoption of ZKP requires less trust, relatively speaking, projects using TEE may develop faster.
The above is the basic structure of Aleo. I will expand the current status of Aleo’s ecological development in future research, and write a special topic to explore how the above-mentioned several business functions of Aleo realize the privacy requirements.
secondary title2. The credit of giant whales is an important factor in this debt crisis. Credit needs multiple middleware and infra to improve. Its core is the credit evaluation system on the chain and off the chain. The credit business on the chain is still looking for PMF
On-chain credit is still in the early stages of the market, lacking a large amount of middleware and infrastructure, and some problems may need to be solved modularly, such as regulatory licenses, mature DID systems, reasonable on-chain credit algorithm models, and so on.
If 3AC's wallet asset price is at its peak, I believe the credit platform will give it a full score. Therefore, before thinking about the credit business, we know that
Let’s talk about the credit system first. The construction of the credit system is inseparable from the question of how the off-chain and on-chain should coexist.
DID products have been exploring how to combine or trade off chains and off-chains. They are still trying to digitize and structure identities as much as possible. However, due to the limited scales and standards that have appeared in the market, DID has not yet seen an adoption higher rate products.
Therefore, the current credit system construction of credit business is more about off-chain evaluation. Off-chain valuation means that the valuation model is a black box, and crypto credit remains a fragile line of business.
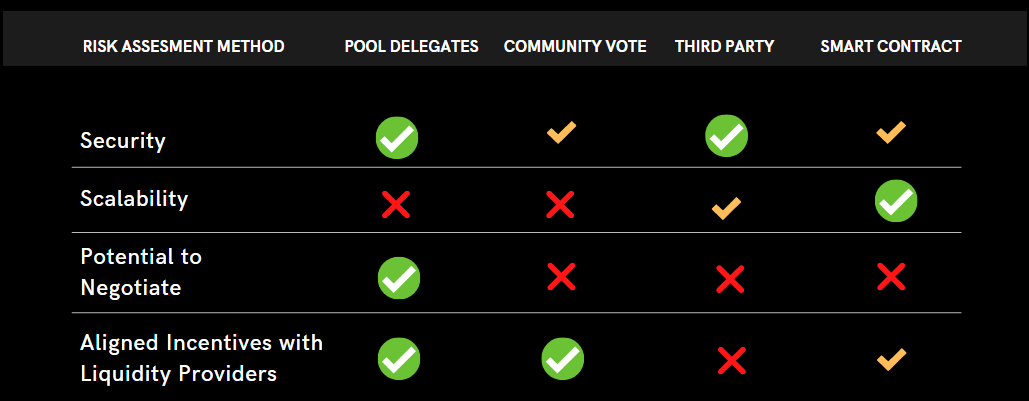
Analysis of different risk assessment methods
We use Maple Finance, Truefi, and Goldfinch three agreements/products to distinguish their credit evaluation methods.
image description
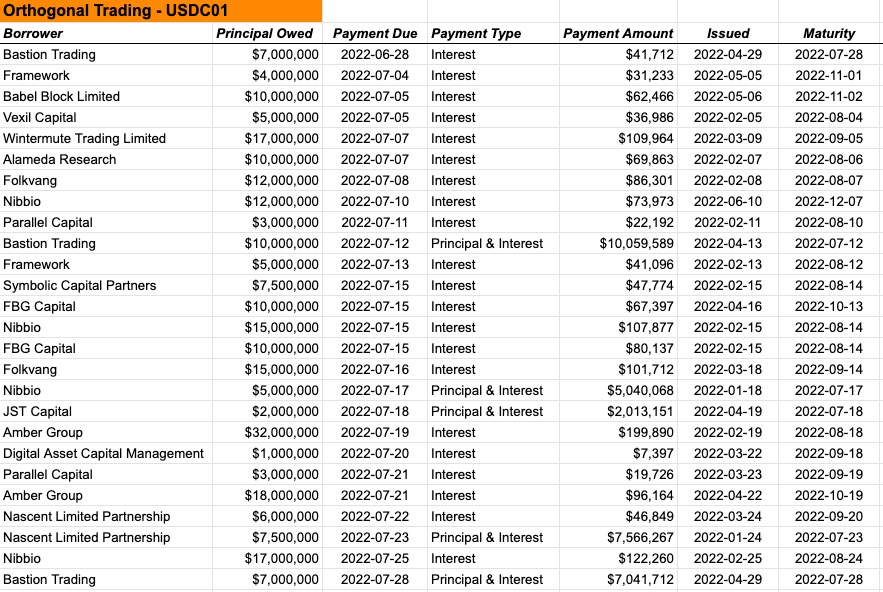
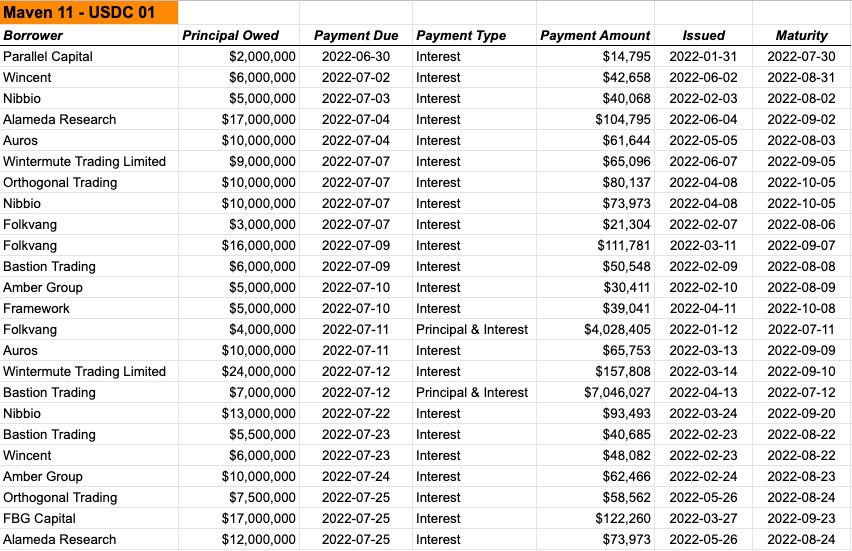
Orthogonal Trading and Maven11 are the main two Pool Delegates
image description
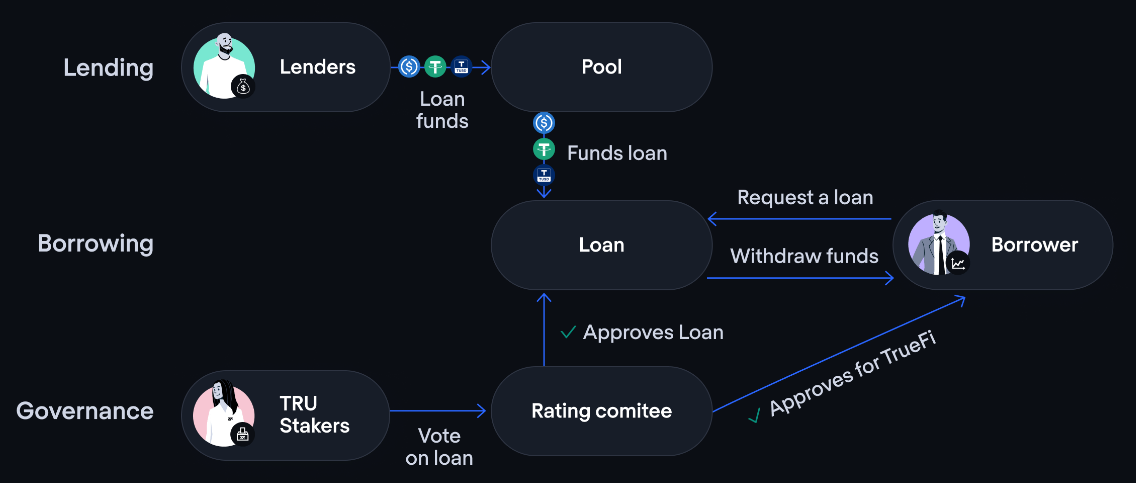
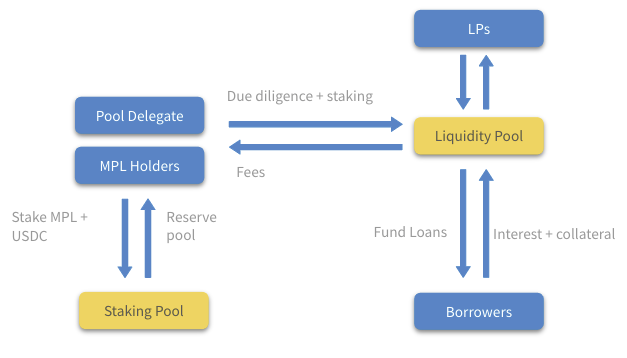
How Maple Finance Works
image description
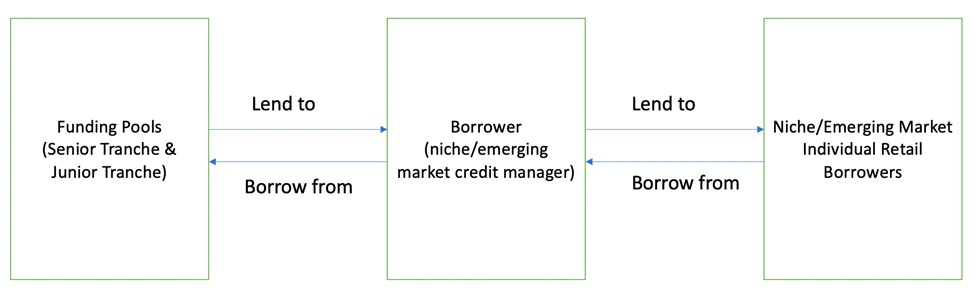
How TrueFi Works
Goldfinch chooses to use a third-party partner team for review and evaluation (Personal or Parallel Markets), and the borrower needs to Stake its token $GFI, which costs about 2 times. Then submit the agency's credit report and financial statement to this team. After a successful review, borrowers receive a non-transferable, unique identity (UID) NFT linked to their designated wallet to avoid Sybil attacks. Subsequently, the system will randomly select 6 of the 9 auditors to approve the loan. (This is similar to Truefi, and it is also an individual who needs to have native tokens as voting rights)
image description
How Goldfinch works
From the perspective of the overall design form, the biggest difference among the three is the evaluation method for loans.
But what they all have in common is that a centralized person/team conducts credit evaluation. Even if it includes stakeholders of token holders, I believe they still feel confused and unknown about the debts of those super giant whales .
So back to the question we just asked.
"If 3AC's wallet asset price is at its peak, how much would Maple, Truefi, and Goldfinch's evaluation model give 3AC?"
Reputation and credit risk scoring on the chain are the main problems, and credit needs to be endorsed by powerful government, state machinery or laws, etc. Credit is not created out of thin air.
What do Maven11 and Orthogonal Trading use to guarantee the endorsement of this credit, is it just an asset put in the pool in advance? UST is a very good attempt. Before LFG bought BTC, I was a believer in Terra, but then I found that the leverage brought by this kind of credit is getting higher and higher. Credit essentially takes time to build and requires constant trial and error. wrong.So why are there still so many mortgage rate models and credit evaluation models in the encryption market, so chaotic?
The essential reason may be that no one can promise what will happen if the money is repaid, and no one dares to bet against what will happen if the money is repaid.
At the same time, because of the large interest rate difference between DeFi and traditional banks, a situation where borrowers are unwilling to pay higher interest rates has also formed. (If the borrowers who are willing to pay high interest rates are likely to be unqualified, there is a certain risk here), forcing Maple and Truefi to use their own tokens for subsidy incentives.
Therefore, the current institutional credit business on the chain is still in a stage of trying to find a PMF.
But when debts are restructured, there will be a new cycle. Credit remains one of the DeFi engine factors that cannot be ignored.
We just mentioned that the interest rate difference between DeFi and traditional banks is relatively large, and the interest rate difference creates borrowing demand.
But at the same time of borrowing assets, it means that you're short, to be precise, you have some implicit short-selling awareness and ideas, or think that its price may be in a state of shock in a short period of time.
This is called carry trade in Tradefi. When there is a huge fluctuation in carry trade, Tradefi's yield drops, which leads to a drop in interest rates in mainstream lending platforms such as AAVE and Compound. And the stable currency in DeFi has the possibility of depeg, because its application scenarios are still limited.
Therefore, when the liquidity is tightened, the user's life may be more denominated in fiat currency, so even if the user lends stable currency such as DAI, it will still be converted into USDC or fiat currency in CEX. Therefore, we will find that more traditional giants and giant whales start to try to short stable coins to cause depeg, which is an opportunity for arbitrage.
Coincidentally, because the credit algorithm model of credit and other businesses is not perfect and other factors, the over-collateralization model of DeFi has become the mainstream to ensure the safety of the lending platform and the liquidity of the treasury to better control risks.
Overcollateralization is not perfect, and its possible risks include:
The over-collateralization model is a blood-sucking bug in some public chains with insufficient liquidity. When you use the chain's native protocol assets to lend a large amount of ETH, BTC, and USDC for cash, you essentially drain the chain's non-native asset liquidity. Some public chains have higher TVL but are mostly native assets that are difficult to realize (unless you are willing to endure extremely high slippage on DEX).
The asset prices in the encryption market may fluctuate violently for a long time, because over-collateralization can easily form a highly panicked run. In order to ensure the safety of the liquidation line, giant whales are likely to sell Alt Coin to gather liquidity to fill collateral.
But relatively speaking, for the crypto market that is still in the extreme dark forest stage, over-collateralization is indeed a better way to control risks. For crypto-native liquidity, the most suitable target should be the stable issuance of over-collateralization For cryptocurrency, serial liquidation may be the best way to evolve Crypto, and whether the collateral can support this banner is also very important.
Not long ago, AAVE announced the launch of its own over-collateralized stablecoin (GHO), which is likely to seize some of the stablecoin market share. It needs to be observed whether GHO can use AAVE's endorsement to quickly establish some application scenarios in several DeFi protocols. Before that, I was still thinking about what kind of bank on the chain lol, and I may have the answer soon.secondary title
3. The flaws in the credit evaluation system reflect the importance of DeFi’s native certification system and decentralized reputation scoring system
Here I choose to share ARCx.
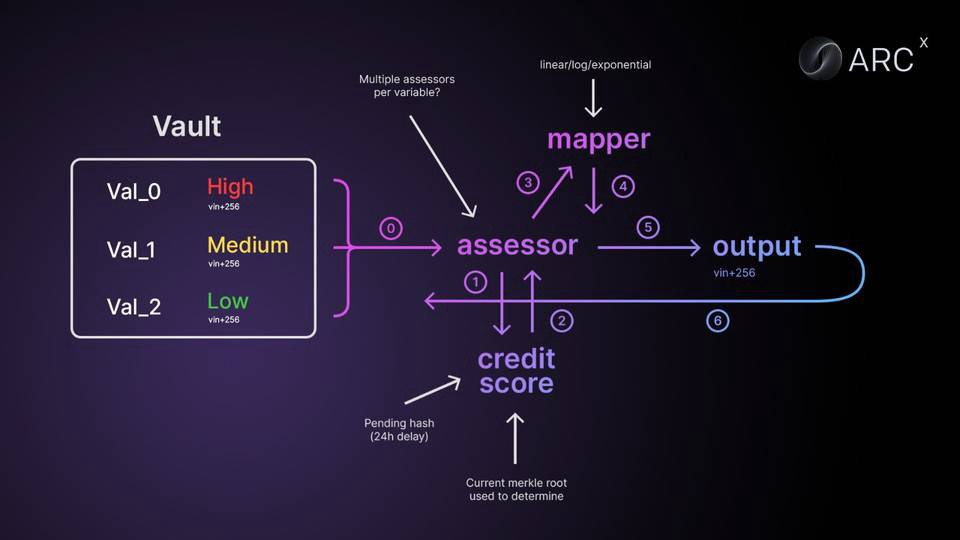
From the Slogan level, it solves my confusion about over-collateralization and privacy, including the credit scoring system of credit, but we still need to observe its adoption rate.
And whether the credit scoring system it designed can really solve the above problems in practice.
It designed a DeFi Passport (0-999 points), ARCx will generate a credit score based on past user interactions with wallets of various DeFi protocols. The evaluation criteria include many variables, such as loans, liquidations, airdrops, and user behavior.
“The DeFi ecosystem is a new quadrant of the financial system, but from a reputation standpoint, it’s an island separate from the mainland. Why?
no identity.
All the work you do to build your reputation in the traditional financial system doesn’t apply because the DeFi ecosystem doesn’t know who you are. It's like switching schools midway through your junior year. Everything you did in the first two years is gone and you have to start over. "
secondary title
4. Through the splitting and digital construction of the word "identity", to make the user's identity and data unique and composable, we need a minimum "DID protocol"
When the word "identity" is placed on the Internet, it seems that we can disassemble it into a combined framework for storing, managing, and retrieving information.
But "identity" involves "philosophy of self". When we discuss "self", we should think of people as a whole. Identity is a person's social attribute, and to a certain extent, it is also a person's value embodiment.
Voltaire wrote about the word "identity" in his Philosophical Dictionary:
"Only memory can establish identity, that is, personal identity."
"Who I am today is clearly the result of what I experienced yesterday and the imprints it left on my body and mind."
Once upon a time, our identities were shaped by religion and totalitarianism. Today, instead of beliefs and emperors, there are many rating and assessment systems.
These have become the invisible shackles that control us. Now, can we make the "self" in the real world more free and easy by deconstructing the word "identity"? Give the recognition of social attributes to network identities that can be constructed and split?
Web3 puts every user and builder in control of their own data, value, relationships, and information. Each user will become a unified discovery point for their own data, and feel the composability between applications and interactions.
This may create a composite experience similar to shared network effects, while isolated ones that manipulate user privacy and data information will become isolated islands. And the decentralized identity system that relies on addresses and NFT as the basis for extension will be very limited."A subjective sense, and observable quality of personal similarity and continuity, coupled with a certain belief in the similarity and continuity of certain shared images of the world. As an unconscious quality of life, this in a It is evident in the young people who discover themselves and their communities. In it we see the emergence of a unique unity of irreversibly given, that of size and temperament, gift and vulnerability, childhood patterns and acquired ideals, and exposes Available roles, career possibilities, choice of values. Offered, mentors found, friendships established and first sexual encounters.” (Erikson, 1970)
0xBcfd stated in his post that we can learn from the flaws of the original cryptographic identity system and see what is needed in a more reliable decentralized identity system. Clearly, a single registry (index), identifier standard, or data structure standard is too rigid.
It must be used with various identifiers. It must be open to a set of flexible, extensible data models and structures. It must work across network environments and networks. Its design should follow
Identity is about the principles of managing and discovering information, so it should put data first.This suggests a simple design: each identifier maintains a table containing its own data. Taken together, these identity-centric user tables form the Internet's distributed user table.
This distributed user table is not an actual table, but a virtual table, which is produced by several components corresponding to the parts of the traditional user table:Identifier
: Decentralized identifiers should not be entries in application databases, but should be provably unique and cryptographically controlled. Accessibility requires the acceptance of multiple forms of identifiers across various networks - similar to the DID standard for decentralized identifiers.Data Structures¶
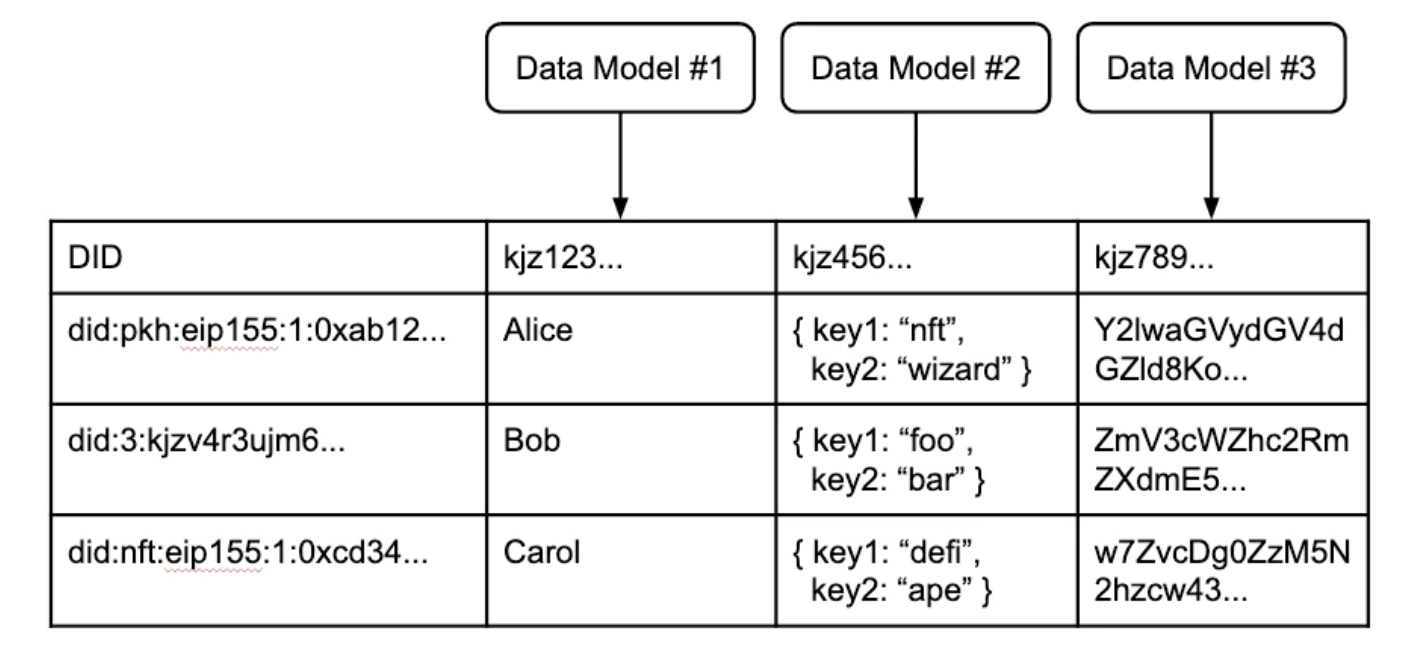
: Similar to how application developers define their own data structures, a decentralized data layer needs to enable developers to define custom data models while ensuring that these models are reusable and publicly stored.
Index
: The user brings their identifier when the application defines the data model. Standard indexes can combine these elements into a user table (or application table) so that when a user interacts with the application (creates data), that information is properly cataloged for future routing. This creates an easily discoverable record of user data - mapped to a data model and cryptographically linked to an identifier.A distributed virtual user table with various DIDs from different networks, developer-defined data models, and related records
Therefore, a reasonable decentralized identity system should have the following three criteria:Trustless (Dependable)
: Runs on a collection of public networks that anyone can participate in, including partitioned or local networks.Flexible
: Applies to any data structure that a developer can define.
Accessible (Accessible): Works with any open network and unique identifier.
And it is supplemented and perfected by other complex factors, such as:Pseudonymous-first
: There is no need to create an account or verify to get started, a user (or other entity) just needs to carry a cryptographic key pair and start accumulating information around it.Generative
: Information accumulates over time, creating an emerging holistic identity.Composable
: Discover and share information across contexts without the need for pre-defined integration or portability standards.
Separable and selective
: Information sets may be encrypted or obfuscated, or separated across multiple identifiers, or otherwise split at the controller's preference.
We need a minimal protocol that establishes the management and routing to trusted data, leaving everything else up to the creativity of developers, making these unique and diverse.
NFT3 allows users to access the protocol in a simple and convenient way and establish their own identity system while ensuring personal privacy and sovereignty.
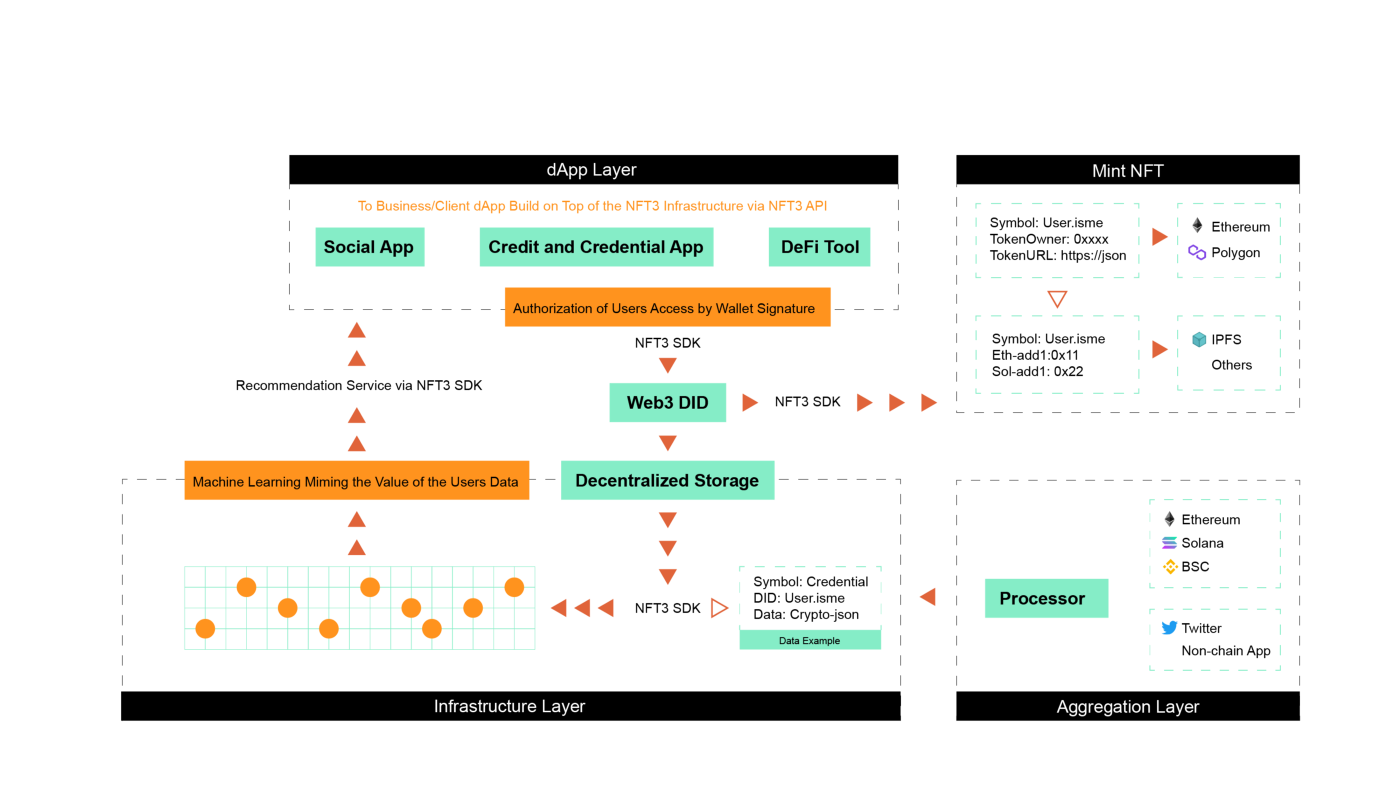
And build a credit scoring system called "NCredit". Higher scores are conducive to higher governance voting weights on the chain, lower interest rates and mortgage rate discounts when borrowing (ARCx also has them), and get more shares when participating in IDO etc.
It provides an SDK to access the developer of the project, and NFT3 is responsible for the gateway of DID. Users can choose to share data according to their own conditions, so any dApp connected to the NFT3 SDK can access it according to the user's wishes.
At the bottom layer, NFT3 is connected to the storage system, and machine learning is performed to imitate user data, and finally transmitted to applications willing to access the SDK, giving uniqueness and diversity to developers and users, and realizing a real minimum identity protocol.
In response to the large-scale liquidation and deleveraging in the market this time, I organized a thinking on the market structure.
So back to the beginning of the article, why does CeFi still have such a large market space?
Obviously, CeFi has its advantages, and I don't think DeFi will completely replace CeFi in the future.
And its slippage is low, those users who have a little understanding of the liquidity pattern of the encrypted market are very suitable for CeFi.
The above is Part 1. I boldly predict that these tracks will have a good growth in demand. But at the same time, the market also needs to prove whether these demands are real and what the change curve of adoption is.
At the same time, in Part 2, I will explain my understanding of the following issues and give examples, especially the part of protocol liquidity health.
secondary title
Questions focus on:
What are the tracks and specific projects that can expand the usage scenarios of Web3?
How do we educate the market, educate users? (This is also the standard I will pay great attention to in the first-level investment recently. Does the team have the awareness of educating the market and target users? And what is their path to do so?)
How can we provide a good environment for developers?
How to make Web3 products have a better retention rate, how to make users change their behavior habits and maintain product sustainability?
The market needs to heal itself, and we also need to sort out our mood and continue to build.
It is not rigorous to understand things and use the current state to deduce the final form, so DeFi still has a long way to go.
Reference:
1. Identity as Information
2. Zero-knowledge-enabled Cooperation: Halo 2 & Aleo | Zooko Wilcox, ECC, Howard Wu, Aleo
3. NFT3 Tech Update
4. ARCX's DeFi Passport Makes It All Possible
5. The Crypto Loan Economy
6. Zero Knowledge Primitives by Aleo





