brief introduction
Original compilation: ChinaDeFi
brief introduction
Phishing on Web3 is on the rise, some of the main phishing techniques include:
Use unsafe Discord bots to post phishing links on some official Discord servers;
Send phishing links directly;
Promotion of fake websites through advertisements on search engines;
Send messages directly via fake Discord bots;
Domain names and content that are highly similar to official domain names;
Use NFT trading platforms such as Opensea to promote fake projects;
suggestion:
suggestion:
Frequently check information through multiple channels, and do not easily trust "bots" or "official links";
Be wary of direct messages: official bots will not ask for verification in DMs;
Double check the domain name or contract address;
Minimize the number of bots in Discord;
Do not bookmark some sensitive websites in your browser.
Definition of Phishing
According to Wikipedia's definition, phishing is a criminal scam that attempts to obtain sensitive personal information, such as usernames, passwords, and credit card details, from electronic communications through a medium masquerading as a reputable legal entity. Phishing is usually done via email or instant messaging. It often leads users to fake websites that look almost identical to real ones to enter personal information. Even with strong encryption and SSL server authentication, it is still difficult to detect whether a website is real or not. Phishing is an example of using social engineering techniques to trick users. It relies on the low affinity of current web security technologies.
In the Web3 world, phishing is mainly achieved through a series of methods such as Discord and website forgery.
Web3 Typical Phishing Cases
This article will reveal several common phishing methods in the Web3 world:
1. Discord bots
On May 23, 2022, Discord's MEE6 bot was attacked, resulting in the posting of phishing information about minting in some official Discord servers.
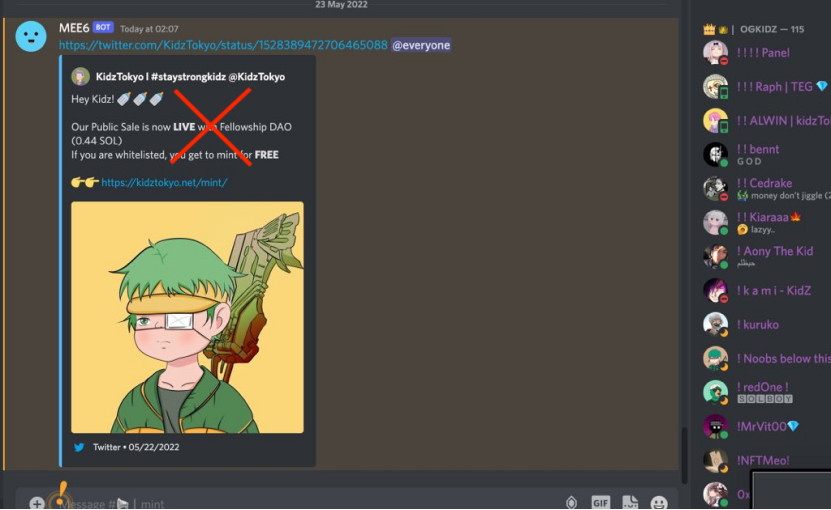
On May 6, 2022, Opensea's official Discord was hacked. The hacker used a robot account to post a fake link on the channel, claiming that "Opensea cooperated with YouTube and clicked on the link to create 100 limited edition mint pass NFTs."
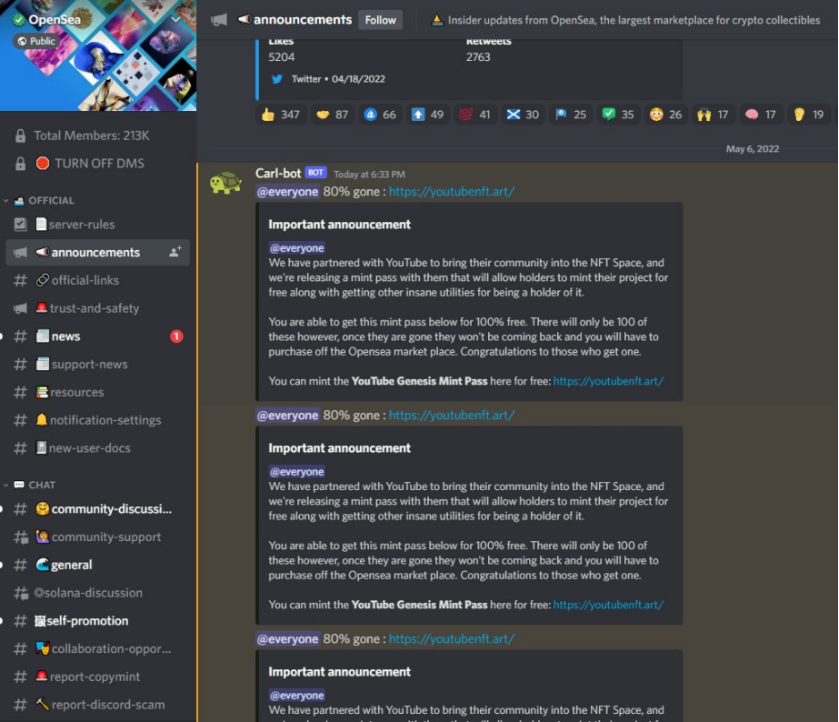
Recently, there have been more and more attacks on official Discord servers, and the reasons may be as follows:
Phishing attacks on employees of the project party, resulting in stolen accounts;
The project party downloaded malicious software, resulting in account theft;
The project party did not set up two-factor authentication and used weak passwords, resulting in account theft;
The project party suffered a phishing attack and added malicious bookmarks to bypass the browser's login rules, resulting in the theft of Discord tokens.
Tips:
Project parties should adopt officially recommended security operations, such as two-factor authentication, setting strong passwords, etc., to protect their accounts; be alert to various traditional network attacks and social engineering attacks, and avoid downloading malware or visiting phishing websites.
Web3 users should be aware that the official version released by Discord may also be phishing information, and the official does not guarantee absolute security. Additionally, wherever we need to authorize or transact ourselves, we need to be more cautious and try to cross-check information from multiple sources.
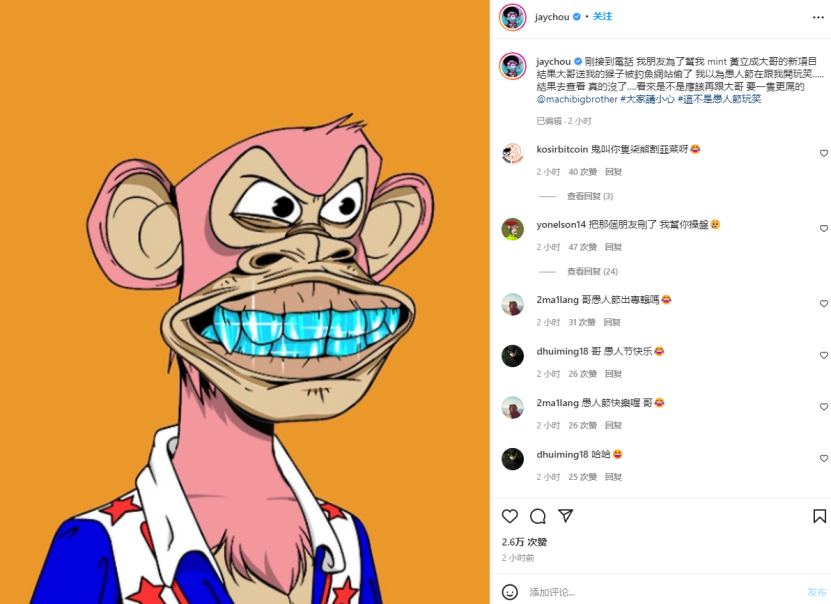
2. Jay Chou’s NFT was stolen by a Discord phishing attack
On April 1, 2022, pop singer Jay Chou revealed on Instagram that his Bored Ape NFT was stolen by a phishing website.
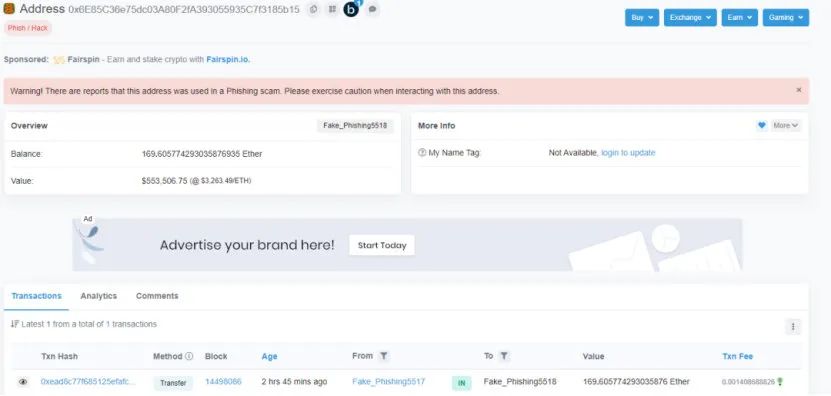
We found that Jay Chou signed the wallet address starting with 0x71de2 to approve the transaction at around 11 o'clock, thereby granting the NFT approval to the attacker's wallet. At this time, Jay Chou didn't know that his NFT was already in danger.
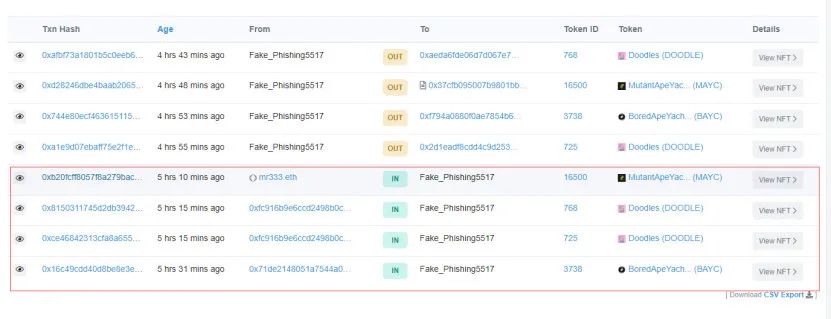
A few minutes later, the attackers transferred the Bored Ape bayc# 3738 NFT to their own wallet address at 11:07, and then sold the stolen NFT on LooksRare and OpenSea for approximately 169.6 ETH.
Tips:
Don't trust private messages easily. Attackers usually lure us to click on links to phishing websites through private messages or emails. All information should be verified on the official website first, and its authenticity should be verified through multiple channels.
The case of Jay Chou being phished was after casting a new project, he may have been less vigilant about phishing attacks at the time. So users must be vigilant at all times to ensure that every step is safe.
3. Phishing Sites on Google Ads
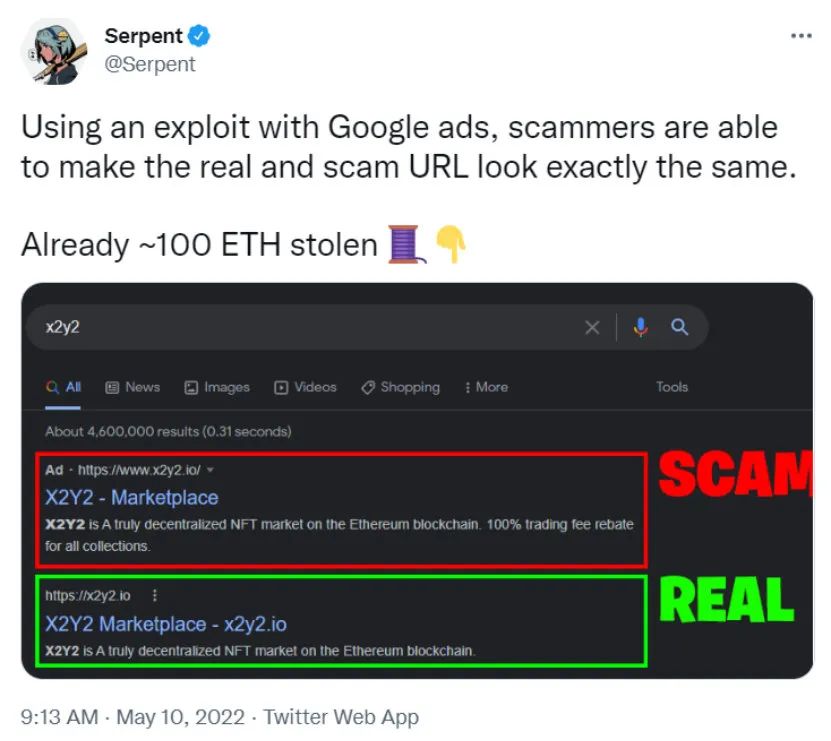
On May 10, 2022, @Serpent tweeted that the first search result on the Google search page for the NFT trading platform X2Y2 was a fraudulent website that exploited a loophole in Google Ads to make the real website and the fraudulent URL look the same , about 100 ETH has been stolen.
Tips:
Search engines are convenient, but not necessarily correct, and the search engine advertising system is easily exploited by malicious websites. Try to enter through the official twitter or Google-certified official website entrance, and cross-check when confirming official information.
Attention to detail. A result from a search engine, if it is an ad, will have the word ad. Avoid clicking on links with the word "advertising."
4. Send private messages through fake robots
Recently, a user joined the official Discord community, and after joining the server, a bot sent a message directly asking for verification.
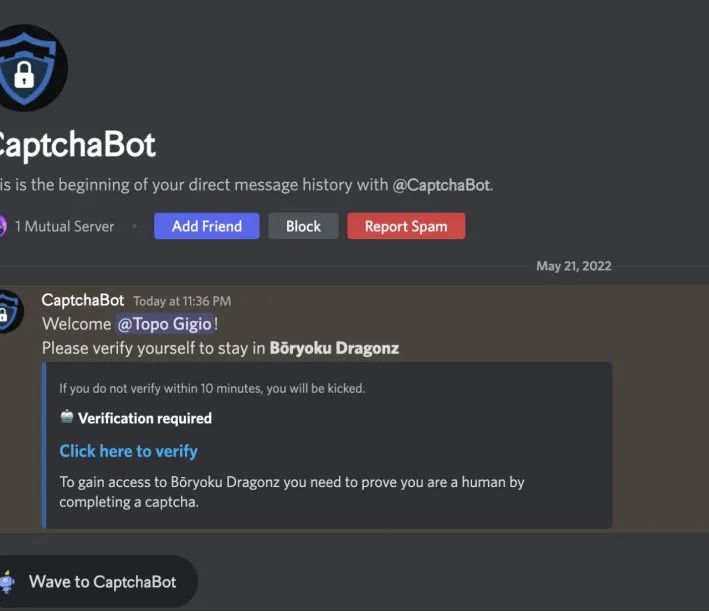
However, when the link is clicked, it automatically pops up the Metamask wallet and asks for a password, at which point the user is almost certain that something is wrong with the site. After debugging and analysis, it was found that what popped up on the website was not a real Metamask, but a fake Metamask wallet interface. If someone enters the password, it will ask the assistant to verify, and finally, both the password and the assistant will be sent to the attacker's backend server, and the wallet will be stolen.
Tips:
Be wary of private messages on Discord: official bots don't ask for verification in DMs.
The authentication process does not require a connected wallet.
Be sure to watch out for odd or unusual behavior, and be sure to cross-validate for more information.
5. The domain name is highly similar to the content
At present, there are various counterfeit websites in the market, most of which imitate official websites with high similarity in domain name and content. This is the most common form of phishing and its main forms are as follows.
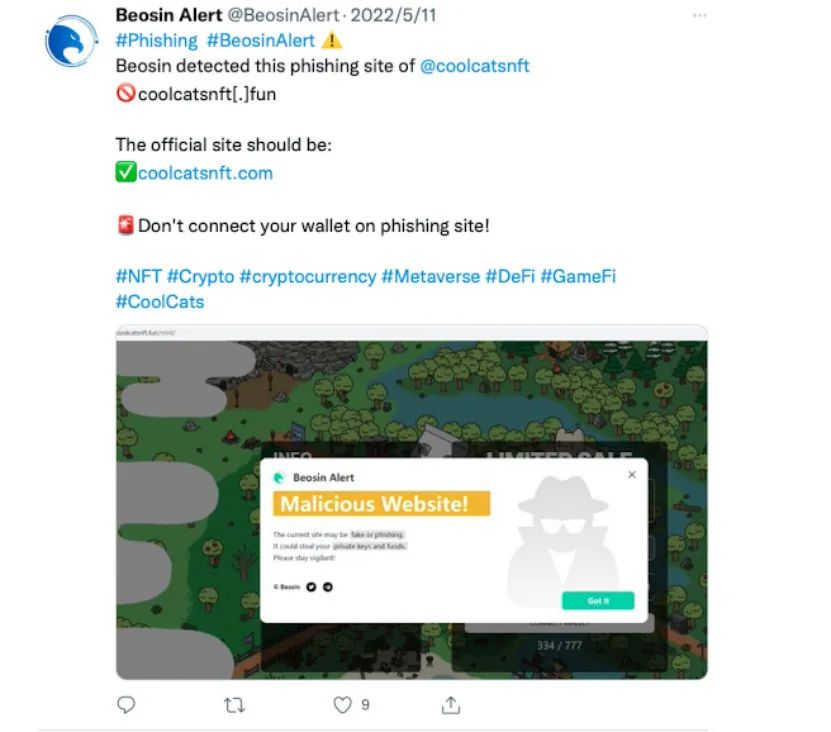
Change the top-level domain name, the main domain name remains the same. For example, the top-level domain name of the official website in the figure below is .com, and the top-level domain name of the phishing website is .fun;
Add some words in the main domain name, such as openesa-office, xxxmint, etc.
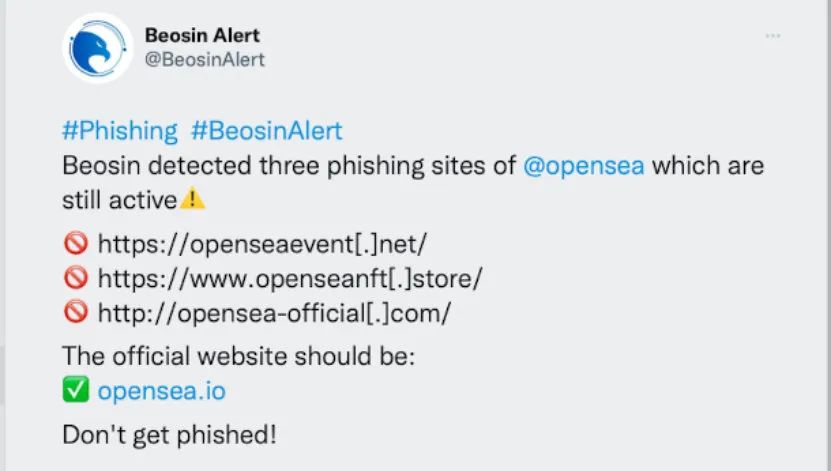
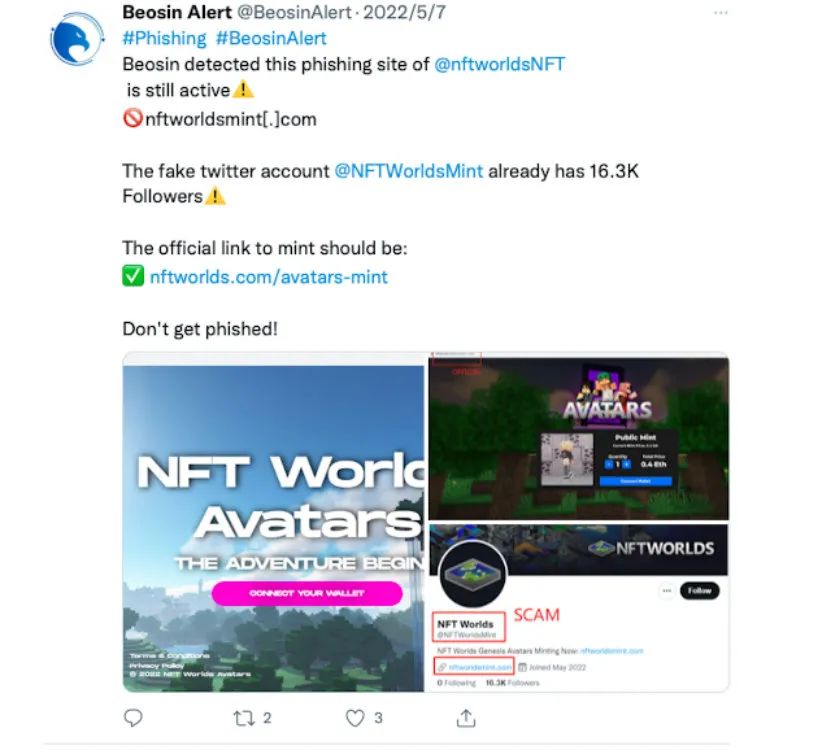
Add a second-level domain for obfuscation and phishing:
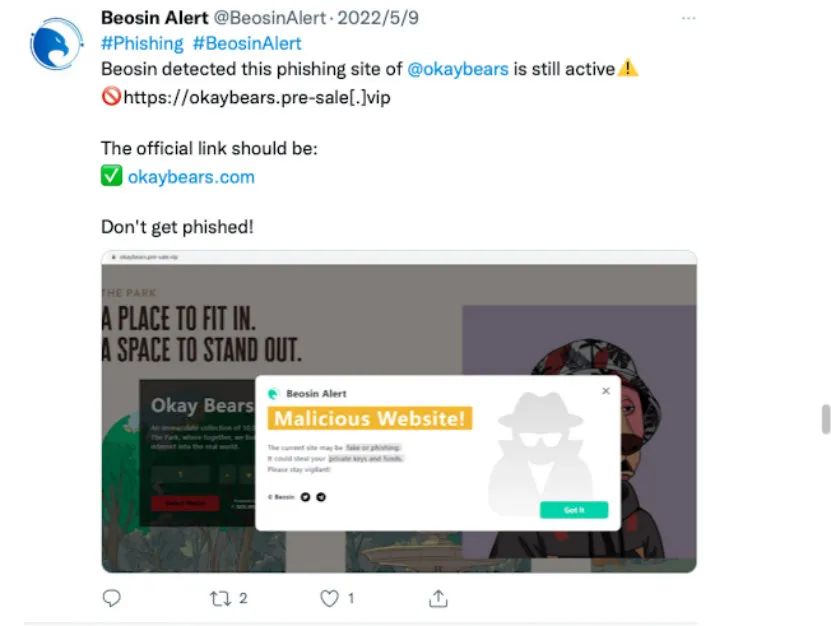
Tips:
When entering a website, first find the official twitter or discord and compare the links one by one to see if they are correct.
Always be vigilant: While these types of phishing sites are the easiest to identify, they are very numerous and can easily trick users if they are not careful.
An anti-phishing plug-in is added to effectively assist in identifying some malicious websites.
6. Fishing items on Opensea
A while back, we found a project on Opensea that wasn't officially open for sale, but had 10,000 items listed. After careful analysis, we discovered a new phishing method. The project first forged a similar official website and a similar domain name using the above method, and then listed a similar project on Opensea, using words such as "free coins" to attract attention.
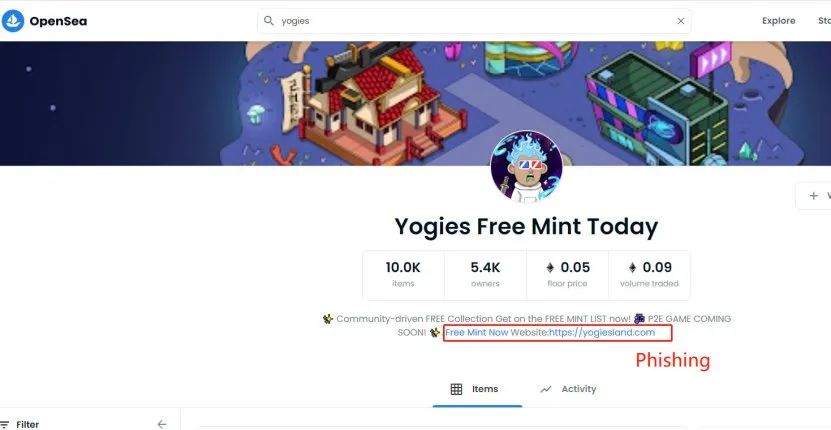
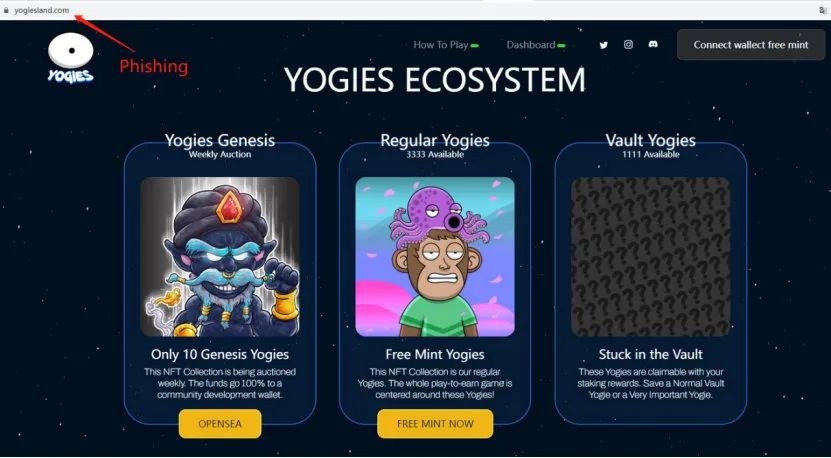
In addition, there are phishing sites and phishing tweets that promote scams:
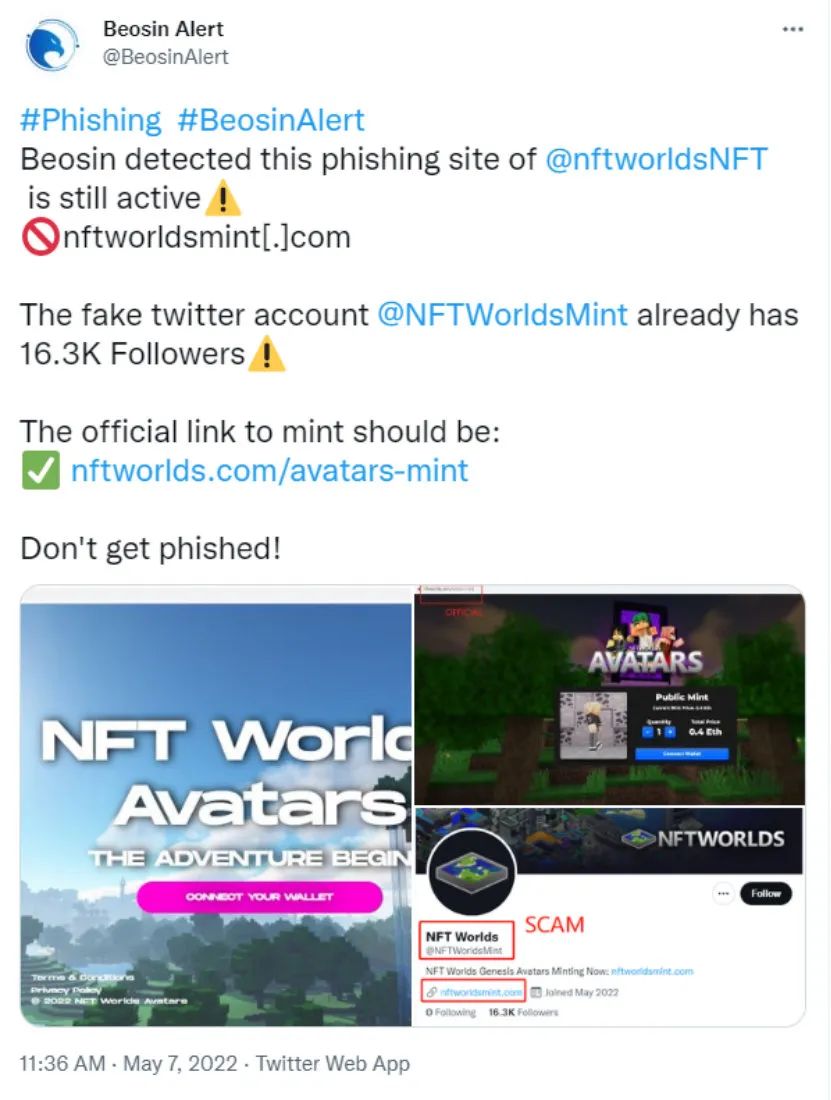
Tips:
Carefully identify Twitter accounts. Sometimes phishing accounts also have a large number of followers, but most of the comments are fake. Or the account was created with an earlier date, but was only recently active, etc.
Projects on Opensea are not always the real projects on the official website. There are still a lot of fake and phishing items on the site, so users need to sift through them carefully.
Always get information from multiple sources. Cross check information from official website, opensea project, twitter, discord, etc. You can also contact the official directly to verify the authenticity.
7. Fake contract address
A new scam that surfaced in March was also eye-opening. The attacker forges a contract with the same number of digits before and after, and uses phishing links to defraud.
The real APEcoin contract address is: 0x4d224452801ACEd8B2F0aebE155379bb5D594381.
The fake contract is: 0x4D221B9c0EE56604186a33F4f2433A3961C94381
This type of attack is uncommon, but confusing. Usually people will check the front and back of the contract address to judge whether it is normal, but few people will check the complete address.
Tips:
For direct transfer transactions, it is best to check that the full contract address is correct.
Solution
Solution
The above only lists the commonly used tactics of phishing scams. However, with the increasing popularity of Web3, there are more and more ways of phishing scams. Users need to remember the above tips. However, in the unlikely event of being scammed, the following steps can be taken to try to remedy it as best as possible:
Immediately isolate the assets and move the remaining assets to a safe place as soon as possible to avoid greater losses.
Post proactively to inform others about scam accounts so you don't endanger your friends and community.
Preserve the evidence as much as possible, and seek follow-up help from the project party or institution.
Find a professional company for fund tracing.
Finally, if you are unfortunate enough to be scammed or phished, it is recommended to document and share your experience with others on social media.





