secondary title
The biggest hacking incident in history
What is the concept of 610 million US dollars? If calculated according to the market price of the relevant assets at the time of the incident, this is not only the largest hacking incident in the history of DeFi, but also the largest hacking incident in the history of cryptocurrency, surpassing the famous Mt.Gox incident ( 744,408 BTC, with a total value of about $400 million at the time), and the Coincheck case in 2018 (523 million XEM, with a total value of about $534 million at the time).
statisticsstatistics, In 2020, there were more than 40 attacks in the DeFi field, with a loss of about 177.4 million US dollars (about 49.39 million US dollars have been recovered). The number of Poly Network’s incident is more than three times that.
Regarding the specific reasons for this incident, Odaily has asked many well-known security companies such as PeckShield, SlowMist, BlockSec, Certik, and Chengdu Lianan. Among them, BlockSec stated to Odaily that the hacker provided a valid signature message to the function "verifyHeaderAndExecuteTx" in the Poly Network contract, and the "onlyManagerContract" modifier in the "LockProxy" contract will not be bypassed.Based on these observations, BlockSec believes that the cause of this incident may be that the private key used for cross-chain signatures was leaked, or that the signature program had a logic loophole that led to the signing of the attack transaction.
This analysis is also basically consistent with the views of some other KOLs. Igor Igamberdiev, an analyst at The Block Research, believes that the root cause of Poly Network's attack is a cryptography problem, which may be similar to the Anyswap hacking incident that happened not long ago-in that incident, the hacker successfully overturned the encryption through a contract loophole. keys, and ultimately stole $7.9 million.
Security researcher Mudit Gupta proposed another possibility. Since the Poly Network contract has only one keeper, except that the hacker may have obtained the key through some means,It is also possible that the hackers collaborated with members of the team to complete the attack, which requires a more thorough investigation.
Dovey Wan, founding partner of Primitive Ventures, also said: "Both Poly Network and O3 (Note: Another major project related to this incident, which will be explained below) are not fully open source, so this is likely to be an internal attack."
--------------------------------------------------------------
analyzeanalyzePoint out: This attack is mainly because the keeper of the EthCrossChainData contract can be modified by the EthCrossChainManager contract, and the verifyHeaderAndExecuteTx function of the EthCrossChainManager contract can execute the data passed in by the user through the _executeCrossChainTx function. Therefore, the attacker passed in carefully constructed data through this function to modify the address specified by the keeper of the EthCrossChainData contract for the attacker. It was not reported on the Internet that this incident occurred due to the leakage of the keeper's private key.
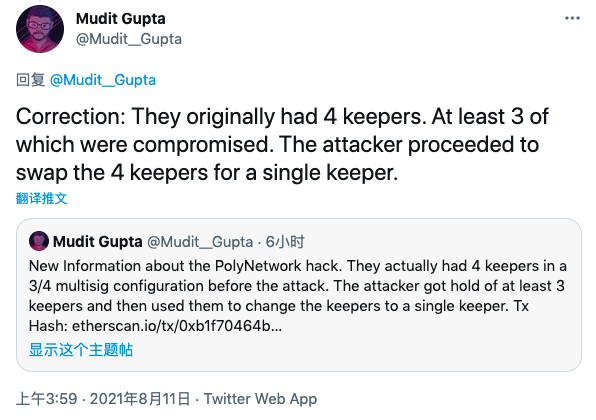
09:50 UPDATE: Mudit Gupta, mentioned above, has since made some corrections to his analysis. Mudit said that he did not agree with SlowMist's judgment, but Poly Network did have four keepers at the beginning, implementing a 3/4 multi-signature configuration. However, before the attack, hackers controlled at least three of the keepers and replaced them with It becomes a single signature, which is why all hacker transactions have only one keeper signature.
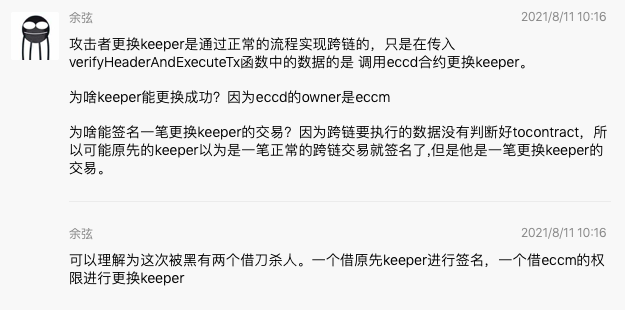
10:25 Update: Yu Xian, the founder of SlowMist, further explained this incident in the community this morning, saying that the attacker replaced the keeper through the normal cross-chain process, but the data passed into the verifyHeaderAndExecuteTx function is to call ECCD (EthCrossChainData) The contract replaces the keeper. The reason why the keeper can be replaced successfully is because the owner of ECCD is ECCM (EthCrossChainManager). The reason why I can sign a transaction to replace the keeper is because the data to be executed across the chain has not judged the tocontract, so the original keeper may have signed it as a normal cross-chain transaction, but this is actually a replacement keeper transactions.
Yu Xian finally concluded that it can be understood that there were two murders with a borrowed knife in this hack. One is signed by the original keeper, and the other is replaced by the authority of ECCM.
secondary title
--------------------------------------------------------------
containment and escape
Hacker address:
Hacker address:
Ethereum address: 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963;
BSC address: 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71;
Polygon address: 0x5dc3603C9D42Ff184153a8a9094a73d461663214.
After Poly Network issued an appeal, various KOLs voiced their support in an attempt to prevent hackers from laundering money.
Changpeng Zhao said on Twitter: "We have been informed of the hacking incident at Poly Network. Although no one can control BSC or Ethereum, we are coordinating with all security partners and we will do our best to help proactively."
OKEx CEO Jay also said: "OKEx has been paying attention to this case, we are observing the currency flow, and will do our best to assist in handling this incident."
the other side,image description
Hackers exchanged nearly 100 million USDC for DAI through Curve.
secondary title
large begging scene
With such a large amount stolen, the number of victims is naturally indispensable (the author of Odaily is also one of them).
As far as the current situation is concerned, the main groups affected by this incident are users who mine through the cross-chain aggregator O3 Swap, and O3 Swap itself has therefore suspended cross-chain related services. Before the incident, the annualized rate of O3 Swap’s stable currency pools on Polygon and other chains could exceed 20%, and the annualized rate of some short-term single currency pools (just closed last week) could reach hundreds of percent. Today, when mine income is declining day by day, this annualized level is quite attractive. A large number of "DeFi farmers" came for high returns, but ended up "losing everything".
The reason why Poly Network was attacked and O3 Swap users suffered is because O3 Swap's cross-chain function is based on Poly Network. In fact, before Poly Network officially confirmed that it was hacked, the main speculation in the community was that the O3 Swap contract was hacked.
In the past when DeFi was stolen and users had nowhere to ask for help, many people would choose to send a transaction to the hacker’s address, leave a message saying that it was their own hard-earned money, and beg the hacker to return the funds. But this time, many onlookers who "watched the excitement and didn't think it was a big deal" made things "changed".
After a certain melon eater "prompted and guided" the hacker whose USDT had been blacklisted and was "gifted" 13 ETH by the hacker, more people who had nothing to do with this incident also began to join this large-scale "begging" "Among them, hackers seek rewards by "supporting" them, and even ask hackers to "pull" their own coins.
Most people who eat melons with average "technical skills" choose to beg directly, such as "Brother, give me some money" or "Brother, please."
Users with better "technology" will choose to tell stories, and even let hackers become their own "angel investors", for example, "I have taken a fancy to a project, if you give me how much money, I will make a decision after I become a success." I will repay you twice”, or say “I am still in school and have a hacker dream, hoping to get financial support from my seniors”.
The users with the best "techniques" don't ink ink marks at all, and just admit their father without saying a word.
secondary title
Is there any hope of recovering funds?
Putting aside all kinds of farce, since the incident has happened, the most concerned thing for all parties is whether the assets can be successfully recovered.
Combining the previous security incidents that have occurred in the DeFi world, it is not impossible to recover stolen funds. For example, the dForce and EMD incidents last year successfully recovered the stolen funds.On the whole, such incidents basically have one thing in common - through tracking, the hacker's identity in the real world was exposed, faced with prosecution and accountability from the project party and damaged users, and finally chose to return the funds voluntarily.
Past cases tell us that although DeFi has achieved decentralization at the interaction level, human beings who are protected and bound by the law are the main players participating in DeFi. Therefore, DeFi is by no means a lawless place. When encountering losses, seeking legal protection off-chain is the most effective solution.
The better news is that the SlowMist security team stated that with the technical support of its partner Hoo and a number of exchanges,The attacker's mailbox, IP, device fingerprint and other information have been found through on-chain and off-chain tracking, is pursuing possible identity leads related to the Poly Network attackers. The SlowMist security team combed and found that the hacker’s initial source of funds was Monero (XMR), which was then exchanged for BNB/ETH/MATIC and other currencies in the exchange, and the coins were withdrawn to 3 addresses. Attack on the chain.
Perhaps feeling the pressure, the hacker also publicly expressed his intention to return part of the funds through a transaction at 00:05 on August 11. At the same time, the hacker also proposed a new possibility, which is to use the funds to issue a new token and operate it in the form of DAO.
However, Hoo, the key partner mentioned by SlowMist, further responded in the community that the hacker just registered an account without KYC in Hoo, and transferred a small amount of ETH as a gas fee, and no funds flowed into Hoo . The most important thing is that the hacker’s account in Hufu does not have real-name authentication, so it is still uncertain whether the hacker’s identity can be successfully located through other information (email, IP, etc. mentioned by SlowMist).
Earlier, Poly Network officials once again called out to hackers in the form of an open letter, emphasizing that hundreds of millions of dollars in funds would be a huge case in any jurisdiction, hoping to use this to put pressure on hackers and gain the opportunity to communicate with them. But as of the publication, Poly Network has not disclosed any other substantial progress.
As the multi-chain structure becomes more and more stable, the cross-chain bridge, as a channel for liquidity between different ecologies, is rapidly expanding in value. From Chainswap, Anyswap not long ago, to Poly Network today, this track has become a "fragrant momo" in the eyes of hackers. The security situation is becoming increasingly severe. Project parties, audit companies, and users all need to be vigilant.
The Poly Network incident is still developing, and Odaily will verify and report any subsequent developments as soon as possible. Please stay tuned.
-------------------------------------------------------
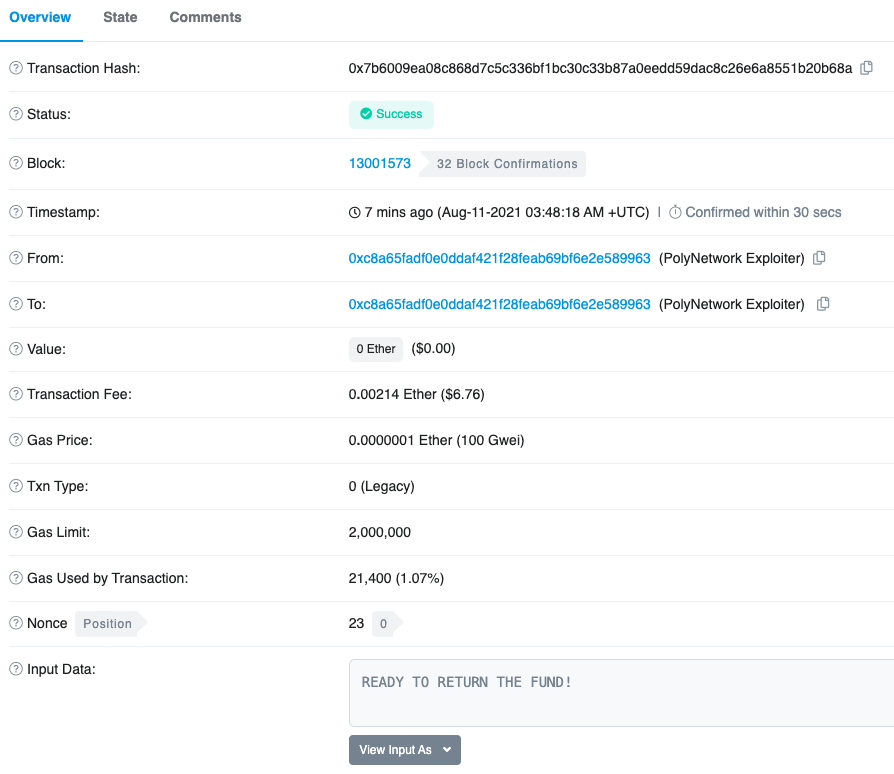
Update at 12:05: At 11:48, the hacker’s Ethereum address indicated through the additional information of a transaction: READY TO RETURN THE FUND! The transaction hash is: 0x7b6009ea08c868d7c5c336bf1bc30c33b87a0eedd59dac8c26e6a8551b20b68a.





