foreword
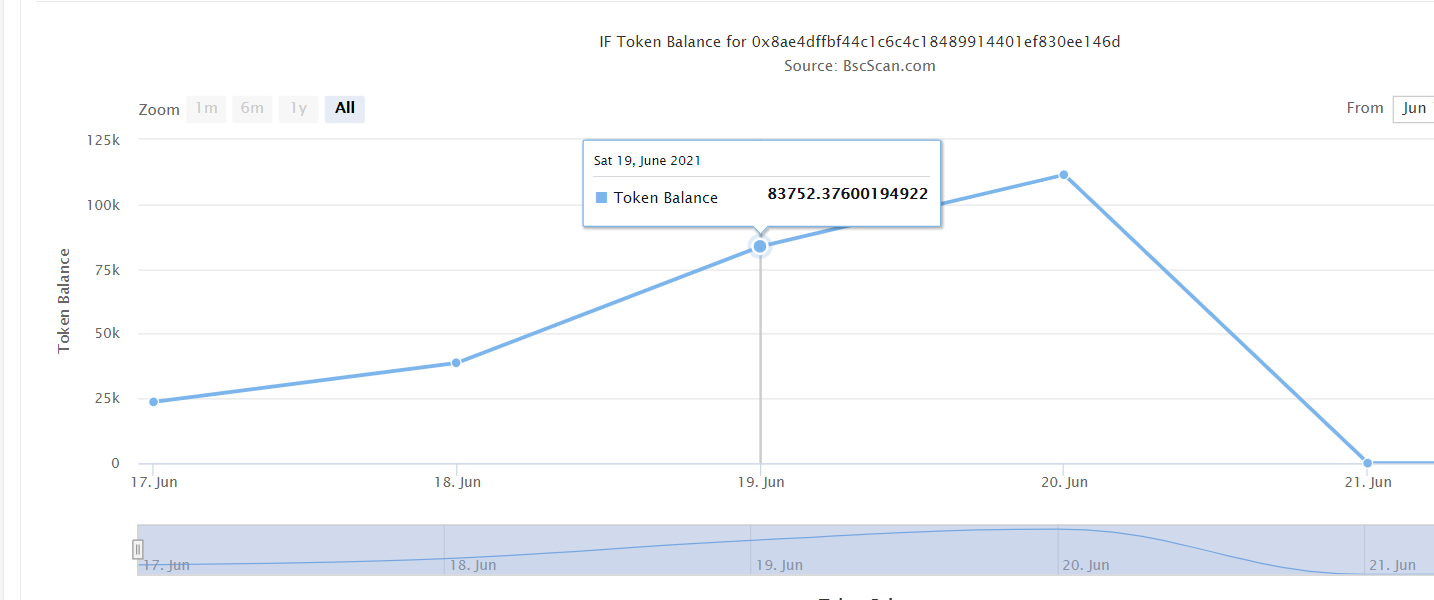
On June 20th, Impossible Finance, a DeFi project on the BSC chain, was suddenly attacked by flash loans. The IF token, which was originally a gratifying rally, has never recovered since then, and its value has been declining. Knowing that Chuangyu Blockchain Security Lab tracked and analyzed this incident for the first time.
event analysis
event analysis
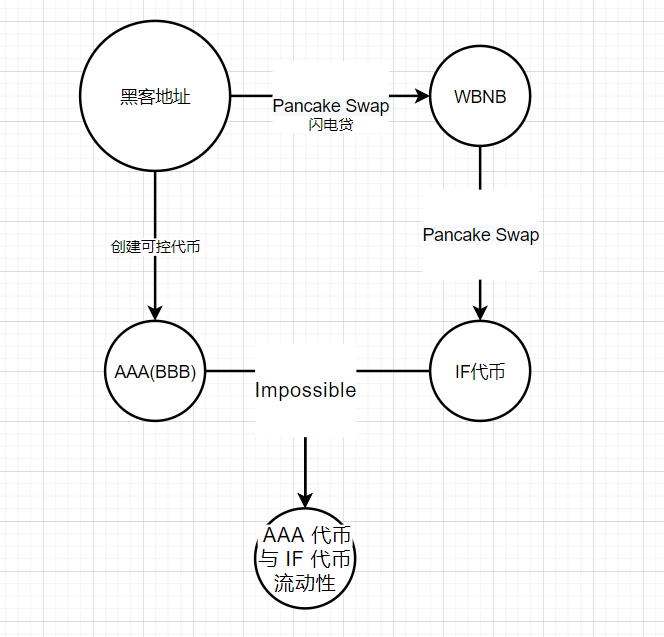
Phase 1: Preparation Phase
image descriptionFigure 1: Flow chart of hacker preparation phasefrom
Hacker Preparation Phase Flowchart
In , we can see that the ultimate goal of the hacker is to create liquidity for AAA tokens and IF tokens.
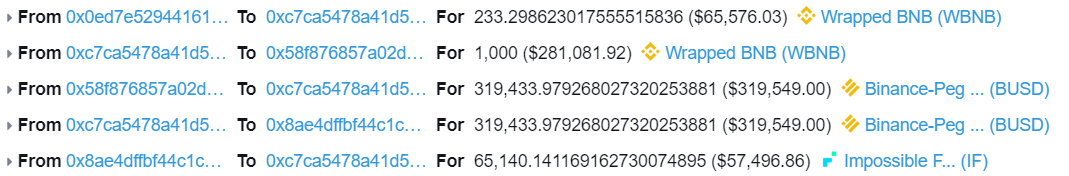
To this end his specific operation:

Step 1: Obtain IF tokens (Use Flash Loan to obtain WBNB tokens from PancakeSwap and exchange them for IF tokens)
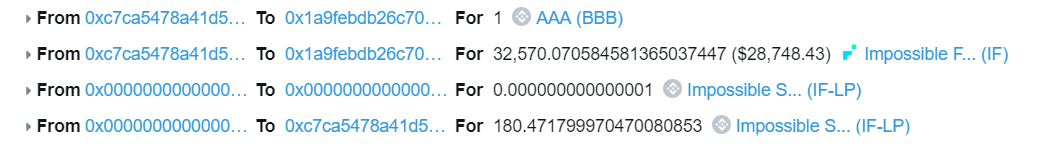
Step 3: Added AAA token and IF token liquidity in Impossible
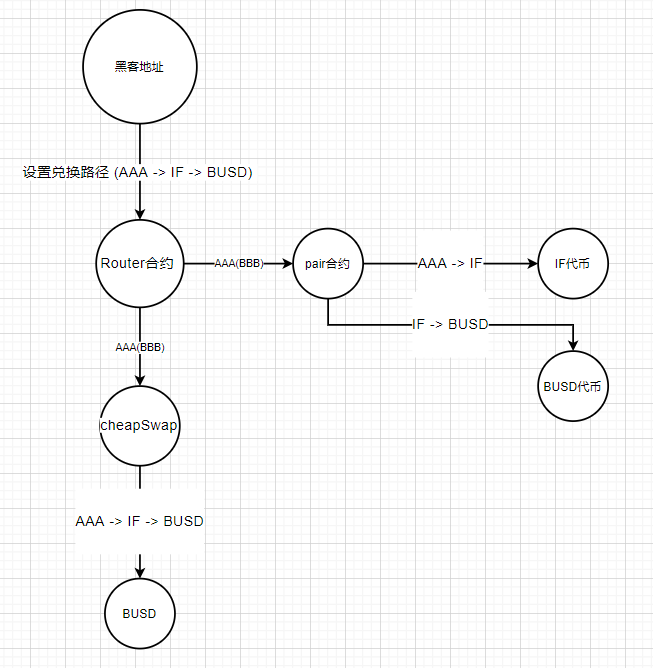
Phase Two: Attack Phase
image descriptionFigure 2: Flowchart of hacking stagesfrom
Hacking Stages Flowchart
In , we can see that the ultimate goal of the hacker is to obtain BUSD tokens. His specific operation:
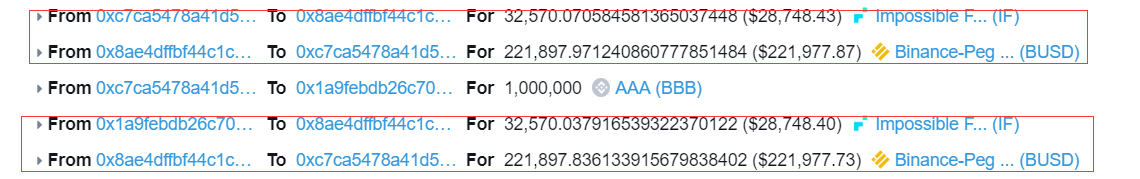
Step 3: Exchange profitable BUSD tokens and exchange IF tokens for the next attack
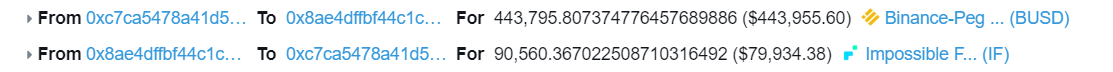
Attack Principle Analysis
secondary title
Attack Principle Analysis
Why do hackers perform two exchange operations in the same exchange process?
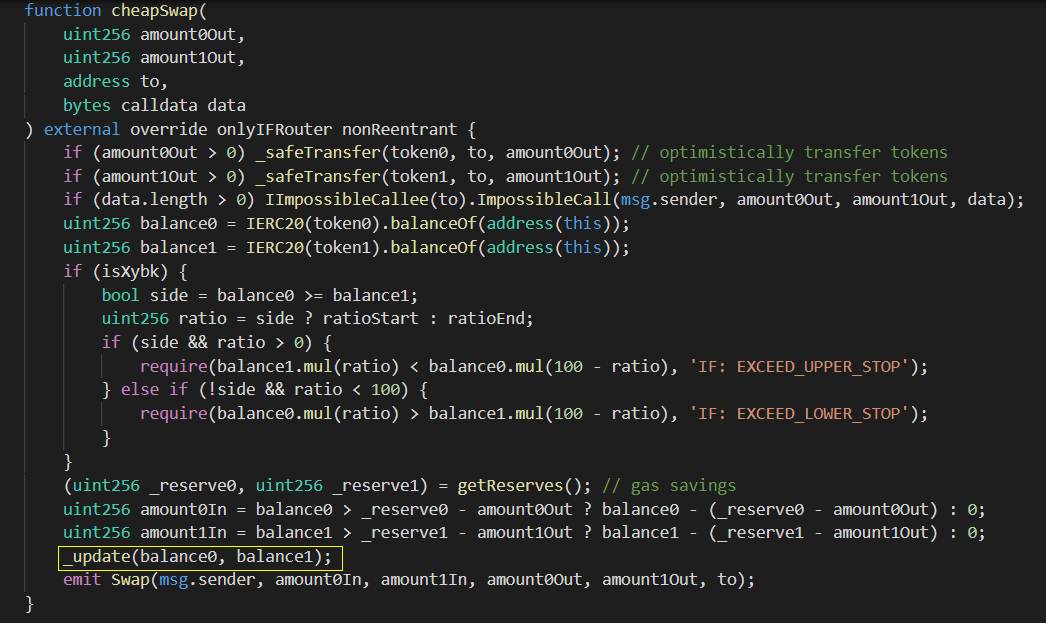
The cheapSwap function does not check the K value change, but directly updates the value change. That's why hackers got extra BUSD tokens through multiple exchange operations.
Summarize
secondary title
Summarize





