secondary title
On May 28, 2021, it was reported that JulSwap, the DEX protocol on the BSC chain and the automated liquidity protocol, was attacked by flash loans.Know Chuangyu Blockchain Security Labsecondary title
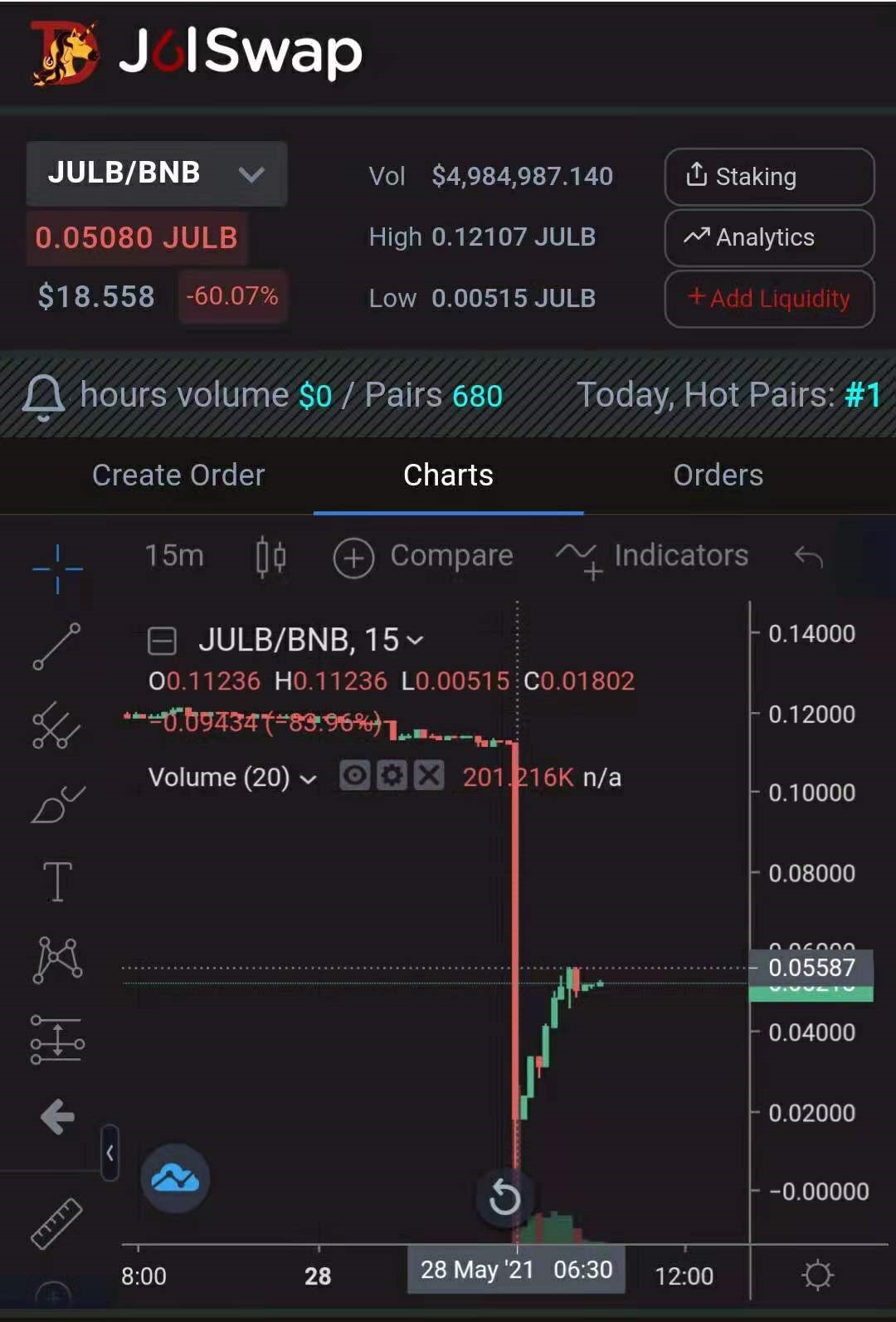
event analysis
Attacker transaction:
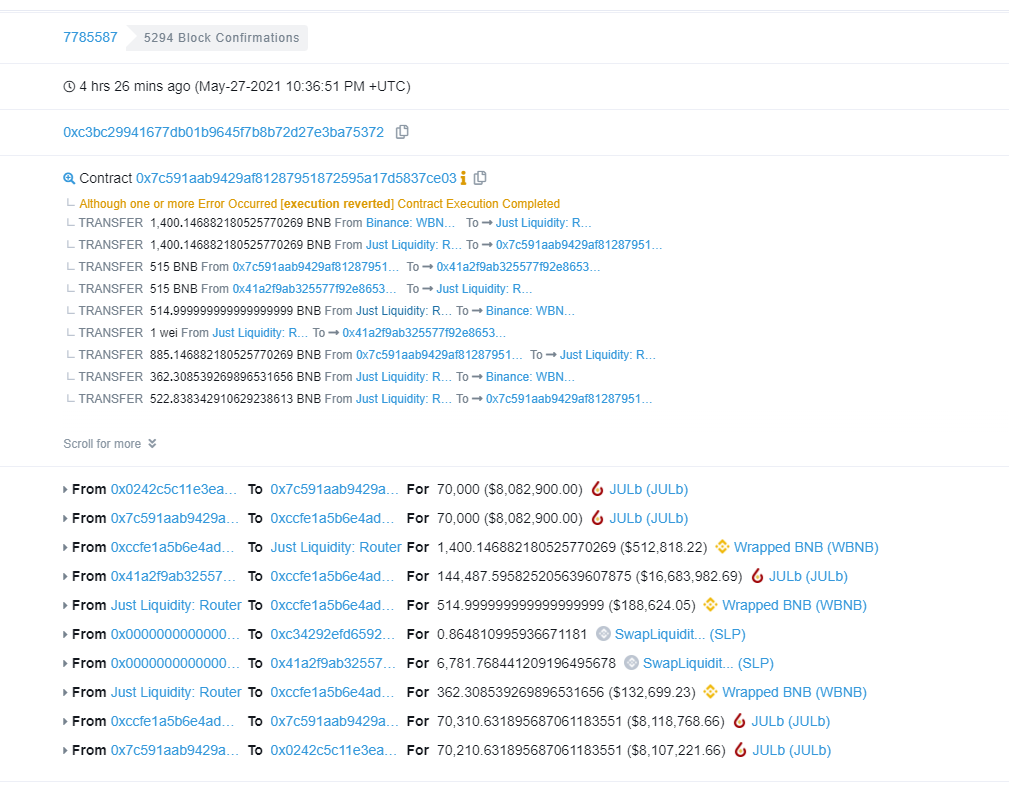
1. Through the transaction records, it can be seen that the attacker borrowed 70,000 JULB tokens through flash loan, and then called the JULB-WBNB transaction pair to exchange to get 1,400 BNB. At this time, there are 1,400 WBNB in the attack contract.
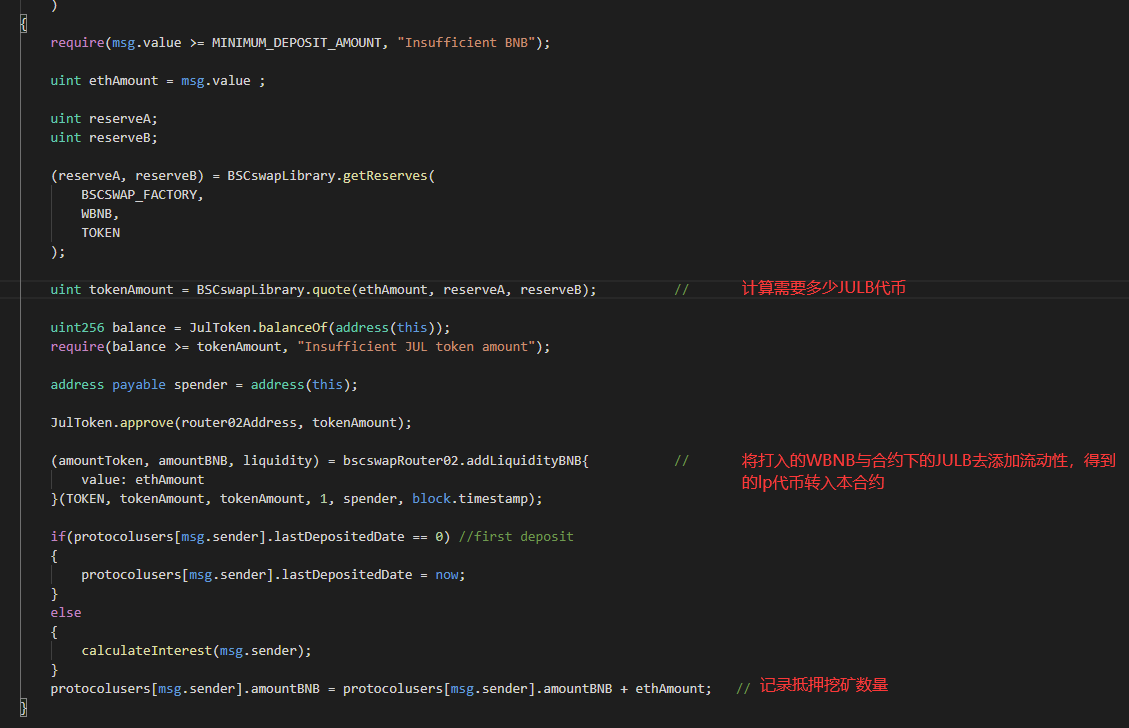
2. Then the attack contract calls the addBNB function of the JulProtocolV2 contract (0x41a2F9AB325577f92e8653853c12823b35fb35c4) for mortgage mining. The function of this function is that by transferring WBNB, the contract will calculate how many JULB tokens are needed to add liquidity mining, and then record the amount of transferred WBNB for mortgage mining. The function code is as follows.
secondary title
Event follow-up