Editor's Note: This article comes fromDODOZooEditor's Note: This article comes from
, Author: Radar Bear, reproduced by Odaily with authorization.
There is a widely circulated article "Ethereum: Dark Forest". In this article, a "universal trading robot" is introduced. This robot will listen to transactions that have been broadcast but not yet on-chain. Once the original transaction is found to be profitable, the same transaction will be sent with a higher gas to grab the transaction before the original transaction.(If you've seen Naruto, it's like copying ninja Kakashi, copying the ninjutsu of Zabuza and preempting it)
The world of Ethereum is like a dark forest full of these robots, and your every move is secretly observed. It sounds like a cold and heartless story, but what we're about to tell is full of warmth and chivalry.
Beijing time on March 9th at 8:00 am.I got a call from the community manager saying our contract was hacked at 5am. I immediately called the technical team to check the situation.Then we found that there was a loophole in the initialization function of the fund pool, which could be called repeatedly. The attacker uses the flash loan to lend the real currency, and then replaces the token pair of the fund pool with the counterfeit currency created by the attacker by re-initializing the contract, thereby bypassing the return check of the flash loan funds.This is not a problem with Peckshield who is in charge of auditing, but that we made several modifications to simplify the code logic before going online, and missed a permission control. We made a huge mistake.Fortunately, this problem only affects part of the business of our V2 fund pool, and the transaction module is not affected. And only the project party is affected, and ordinary users have no loss.We started remediation immediately. The technical team rescued all the funds that still had loopholes (about 80,000 US dollars) within 15 minutes. Afterwards, the pool building entrance was closed on the product, and the operation terminal issued an announcement to notify users and project parties of the progress of the matter.
At the same time, we counted the losses, USDT, ETH and project tokens worth about 3.8 million US dollars. Immediately after that we began to trace.
At 8:30 am on March 9th, Beijing time.Within half an hour after the incident, I received a private message from the white hat samczsun, saying that a mysterious person who did not want to be named, let us call it Mr. Cheetah, "accidentally obtained" one of the sums worth 189w The stolen funds and entrusted samczsun to inform us that they are willing to return the full amount to us.
Who is Mr. Cheetah, how did he obtain part of the stolen funds, and does he know the whereabouts or clues of the remaining stolen funds?
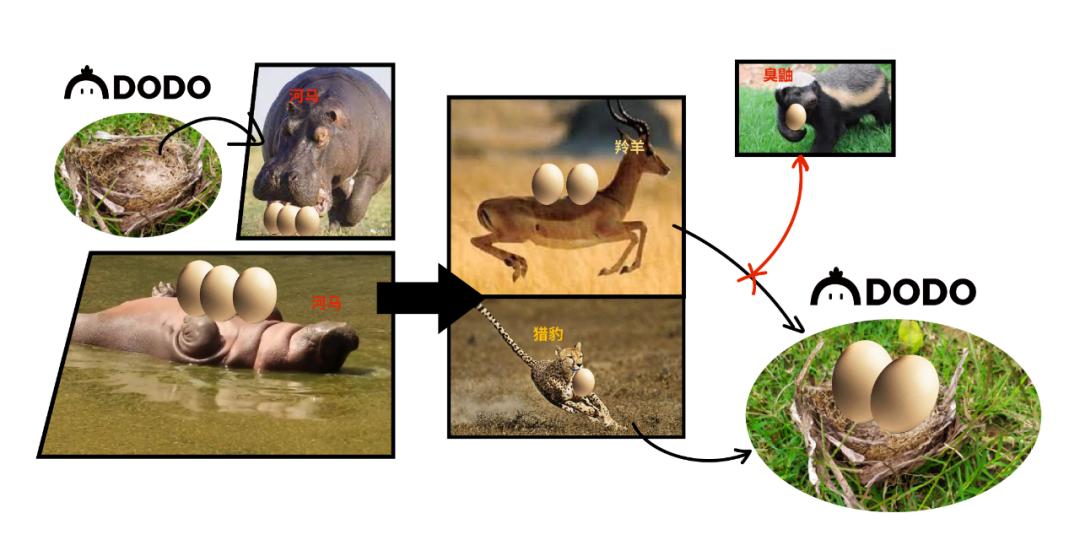
confusing course of eventsAfter analyzing the attack event, we found that there were two addresses that carried out the attack, which we called Mr. Hippo (0x368) and Mr. Antelope (0x355).Mr. Hippo performed two attacks. Among them, 200,000 US dollars entered the centralized exchange, and we immediately contacted the exchange to freeze it. And another sum of US$189w coincides with the amount that Mr. Cheetah wants to return to us. So we speculate that Mr. Hippo should be Mr. Cheetah, and he is probably a white hat hacker.
Mr. Antelope does not seem to be a bad guy either. His attack was realized through a "universal trading robot". It took a gasPrice of up to 90,000gWei to send the transaction, and the miner's fee for a single transaction was as high as 8ETH. Judging from the clues on the chain, it is very likely that Mr. Antelope's robot automatically preempted the transaction of the attacker Mr. Hippo, and Mr. Antelope may not know it yet!
This is another good news for us. If Mr. Antelope can be contacted, the money may be recovered.
the mystery is getting bigger and biggerBeijing time on March 9 at 21 o'clock in the evening.After waiting for a day, we received a refund from Mr. Cheetah ($189w), and at the same time received a message: Mr. Cheetah does not admit that he is Mr. Hippo.
Now the mystery becomes even bigger, there are at least three parties involved in this attack! Also, we don't know how Mr. Cheetah acquired Mr. Hippo's assets. At that time, the only person we had a chance to establish contact with was Mr. Cheetah, who was familiar with the laws of the dark forest.
Although Mr. Cheetah wishes to remain anonymous, through samczsun and some friends, we have communicated our intention to establish a direct connection with Mr. Cheetah. After waiting for several hours, I received a private message on telegram.
March 10th, Beijing time at 1:30 a.m.I never expected that Mr. Cheetah is an old acquaintance I know. I have known him since 2018, when I was still doing development work at DDEX. We will discuss contract development issues together. I lost contact after I left DDEX, and he didn't expect me to become the founding partner of DODO.Mr. Cheetah told me that Mr. Hippo was the attacker. He transferred the money obtained from the attack into a contract, and this contract has a loophole, and anyone can withdraw coins. Mr. Hippo was snatched away by Mr. Cheetah's robot when he was withdrawing coins, thus "accidentally obtained" the funds.
And what about the remaining stolen funds? When we were discussing how to contact Mr. Antelope, he took the initiative to contact me.
March 10th at 3:00 am Beijing time
Mr. Antelope sent me an email anonymously and expressed his willingness to return the funds (worth about 1.2 million US dollars). I finally breathed a sigh of relief, and the two most important parts have been returned. Moreover, Mr. Antelope revealed to us a lot of events he monitored, so that we can finally see the whole picture of the event.
- (here we don't list the very specific txHash because our friends want to keep it low-key)
- The real attacker is Mr. Hippo.
- He executes two attacks, but is outmaneuvered by Mr. Antelope's robot.
- Frustrated, Mr. Hippo took a moment to write a contract to bypass Mr. Antelope's trading bot, and this time he succeeded. Funds fell into Mr. Hippo's contract.
- But when Mr. Hippo withdrew the coins from the contract, he was intercepted by Mr. Cheetah's trading robot again! Mr. Antelope and Mr. Cheetah had a gas battle, and Mr. Cheetah finally won. So far, Mr. Hippo has executed 3 attacks, but found nothing, all of which were snatched away by the robots in the dark forest!
Subsequently, Mr. Hippo carried out two successful attacks, but the amounts were relatively small, and he gained a total of about 200,000 US dollars. we are still chasing the money
Ultimately, within 24 hours of the attack, we recovered $3.1 million of the $3.8 million stolen.
There are many hunters in the dark forest, but they are not as cold and ruthless as popular imagination. Some hunters are gentle big herbivores, knights of the dark forest, intercepting stolen money from hackers and returning it to victims.To this day, many people still think that the digital currency world is full of scammers and hackers, and is bound together with words such as illegal transactions, fraud, and rights protection. But in fact, there are many different roles in this forest: DeFi project parties, ordinary users, enthusiastic people eating melons, arbitrage robots with excellent martial arts skills, white hats who keep vigilance and neutrality in real time, and amateurs who are not necessarily precise and ruthless Hackers, skilled professional hackers...
Together, they form an ecology with its own justice and morality, and each participant more or less plays the role of a law enforcement officer. For honest developers, it's a warm dark forest.
Thank you everyone
A difficult one, P Plus support. After being attacked, we got help from many friends. I am very fortunate that there are so many good people in the Ethereum community. They helped DODO in the most difficult time. We pay our highest respect to the knights and righteous men in the Ethereum community . These include:
samczsun、Tina
1inch、Tokenlon、Binance、Huobi、Etherscan
There are also many friends who have encouraged and comforted us, even in competition, they have stood with us in this critical moment. This makes us feel that there are many warm things hidden under the cold code, such as the praise of honesty, the yearning for fairness, and the cherishment of reputation.
Before Mr. Antelope returned the vETH, his robot fell into a honeypot trap specially designed for him.This trap used 0.05ETH as a bait to defraud 324 vETH, worth about 500,000 US dollars. We don't know who designed this trap, it may be the unwilling Mr. Hippo, or it may be some spectators.
In the end, Mr. Antelope generously shared the loss with us.FlashbotsOn the other hand, some researchers are building a "portal" in the dark forest, such as the MEV Research Institute





